Abstract: Passphrase can ensure the safety of your assets even if seed phrase is "leaked".
In most users' minds, the seed phrase is the "ultimate key" to an encrypted wallet : whoever gets the seed phrase owns everything in the wallet.
This statement is true in most cases, but it's not complete. Because above the seed phrase, there's actually an even more "extremely secure" layer of design— the passphrase .
If we were to summarize its positioning in one sentence, it would be: Passphrase = a double buff of "brain wallet" + "seed phrase wallet".
It's not meant to replace seed phrase, but rather to give it an extra layer of seed phrase in your mind when facing "real-world risks."
Let's start with an intuitive analogy: Why are seed phrase alone not enough?
The security model for seed phrase essentially boils down to who controls the assets – whoever possesses the seed phrase controls the assets .
This model is very effective in preventing cyberattacks and remote hacking, but it has an inherent weakness in the real world:
A seed phrase must be something that can be physically obtained —written on paper, engraved on a steel plate, or taken out and photographed by someone.
This is why in the security community, an extreme but real scenario is often mentioned: when the attack does not occur on the blockchain but in real life, the seed phrase itself becomes vulnerable.
Passphrase exists precisely for this scenario. It's not a feature exclusive to any particular wallet type, but rather a universal security mechanism built upon seed phrase. Whether used in a software wallet or with a hardware device, the underlying logic of Passphrase remains completely consistent; the only difference lies in the level of security boundaries . In practical use, this mechanism is often first encountered by users in the form of a "software wallet." For example, in the SafePal App, Passphrase can be enabled when creating a new wallet.
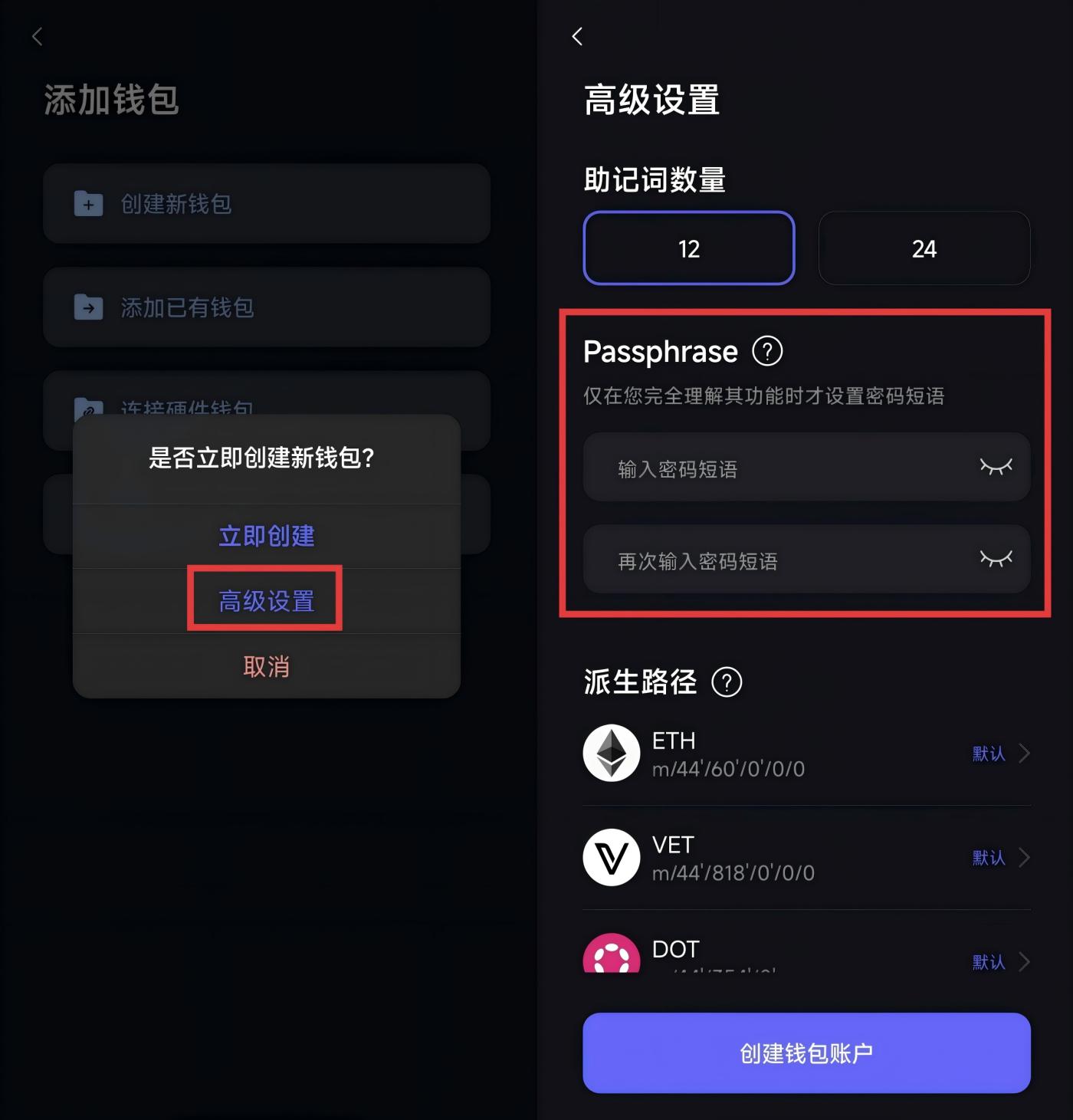
Passphrase's core logic: On top of seed phrase, add another "memory lock".
Technically, the function of a passphrase is very simple, but its effect is extremely counterintuitive. The same set of seed phrase will generate completely different and independent wallet accounts depending on whether the passphrase is entered or not .
You can understand it this way:
- Only the seed phrase → One "default wallet"
- Seed phrase+ Passphrase → A brand new "hidden wallet"
Moreover, as long as the Passphrase is different, even if it differs by only one character, completely different account spaces will be generated .
Once you understand this, its performance in higher-security scenarios becomes more intuitive. When used in conjunction with a hardware wallet, the boundaries of this security model are further expanded. This is why Passphrase is most often used in long-term holding or high-value asset management scenarios. For example, you generate a seed phrase offline using SafePal X1 and securely store it on the hardware device; on top of that, you set a Passphrase that only you know, such as: SFLRW,HKJZ (an abbreviation of "数风流人物,还看今朝"). This creates a completely different account space.
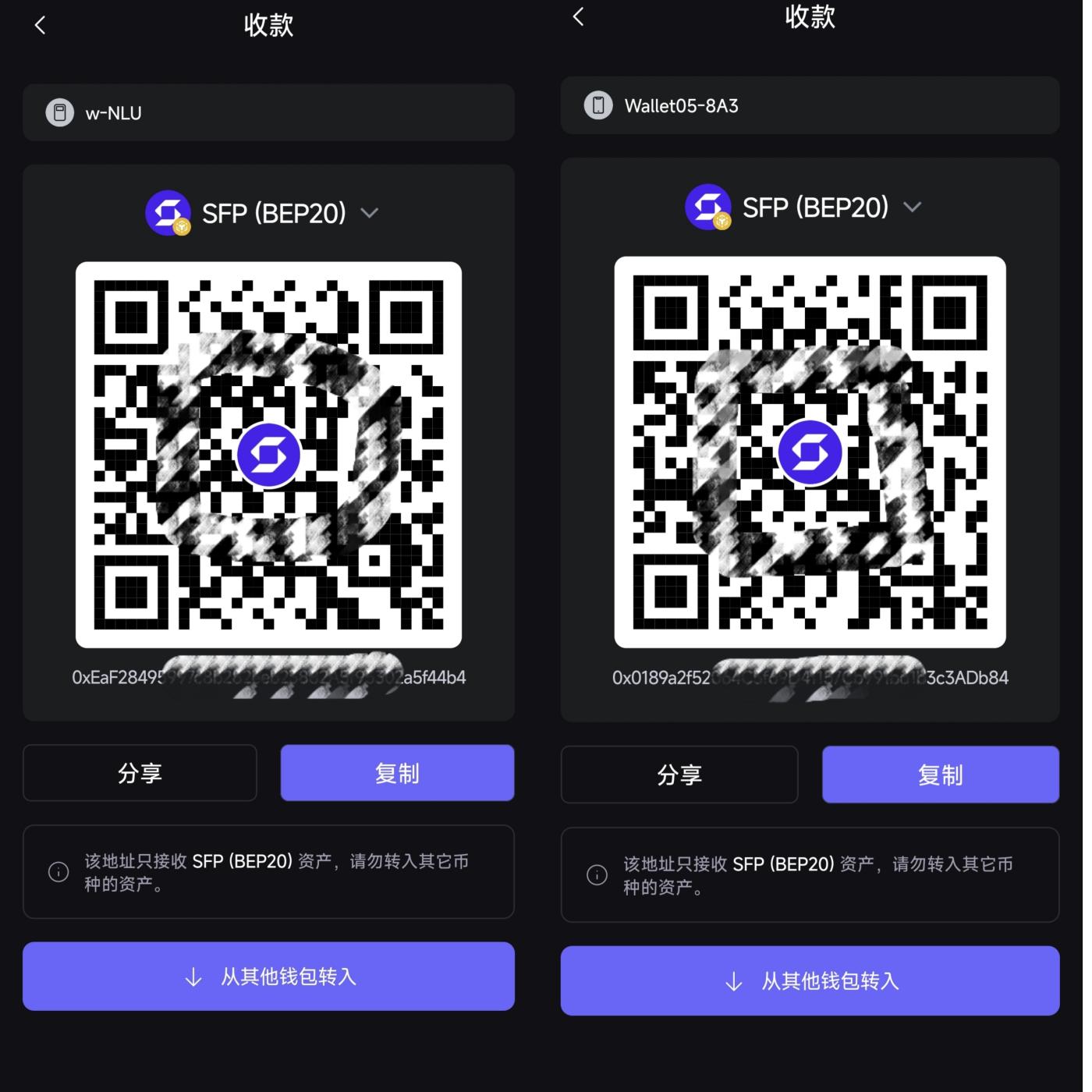
(The first address did not have a passphrase set, while the second address did.)
Moreover, this string itself doesn't need to be "good-looking" or understood by anyone, but as long as it only exists in your own memory , the wallet derived from it can only be accessed by you.
Why is it described as having the double benefit of "brain wallet + seed phrase wallet"?
If we consider the preceding discussion within the same security framework, hardware wallets address the issue of keeping private keys and seed phrase away from the internet, thus reducing the probability of remote attacks.
Passphrase addresses a completely different problem: even if the physical carrier is removed, the asset remains unreachable.
When the two are combined, the security model undergoes a qualitative change:
- Hardware wallets provide physical isolation
- Passphrase provides memory isolation .
Passphrase doesn't exist on the device, on paper, or in any seed phrase backup. It only briefly participates in the derivation process at the moment you type it.
This means a very crucial conclusion: even if someone gets your hardware wallet and even knows your PIN, they cannot access the corresponding hidden account unless they know the passphrase.
In which real-world scenarios does the value of a passphrase manifest itself?
To truly understand the value of Passphrase, one often starts not with its "technical principles," but with its use cases .
For users who hold long-term positions or high-value assets, it solves at least three types of practical problems.
First, it hedges against the risk of seed phrase leakage. Even if the physical backup of the seed phrase is photographed or stolen, the truly important assets can still be stored in the Passphrase wallet, not exposed to the same risk level as the "original account".
Secondly, there is the control of privacy and boundaries. Even family members and friends, even if they have legal access to the device itself, cannot see or operate the hidden account unless they have a passphrase.
Third, there is flexibility in asset management. By using different passphrases, you can create multiple logically independent accounts under the same set of seed phrase for long-term reserves, daily use, or asset segregation at different risk levels.
From this perspective, Passphrase doesn't make wallets "more complicated," but rather makes the way high-value assets are stored more like the logic of a real-world safe .
However, it must be made clear that Passphrase is not suitable for everyone.
At this point, many people might have an impulse: "Should I add a passphrase to my wallet right now?"
The answer is actually: not necessarily, and it's not suitable for many beginners.
The reason is simple, and also cruel— once a passphrase is forgotten, there is no way to remedy it.
It is not saved in a Web3 wallet, nor can it be "recovered" or "reset". Entering the wrong passphrase will not prompt you with an error message; it will simply take you to a completely new, empty wallet. In the real world, a large number of users have permanently lost their assets not because of hacking, but because they forgot their passphrase .
Therefore, Passphrase is more like a "high-risk, high-reward" tool:
- It can raise the safety threshold to a very high level.
- However, at the same time, the "cost of operational errors" was also maximized.
In conclusion: The right mindset for Passphrase
If you had to summarize Passphrase's positioning in one sentence, it would be this: it's not a "standard" feature of crypto wallets, but rather an "advanced option" for a very small number of people.
Before you decide to use it, you should ask yourself this question: Will I still be able to remember it accurately three or five years from now without any prompts?
If the answer is no, then perhaps not using a passphrase is the most responsible choice for your assets.