In this week’s Security Digest, Verichains announces the discovery of critical key extraction attacks impacting multiple vendors and billions of dollars of assets at risk.
Insights into Responsible Vulnerability Disclosure, and the meticulous coordination required to ensure safety during disclosure and remediation for all vendors.
What is TSS and MPC?
Multi-Party Computing (MPC) is a cryptographic protocol that allows a group of parties to securely generate a signature on a message without revealing their individual secret keys. It is commonly used by multi-party wallets and digital asset custody solutions and has quickly become the standard for securing digital assets by major blockchains and financial institutions.
Threshold Signature Scheme (TSS) is a cryptographic protocol that enables a distributed set of signers to control funds by cooperating to authorize transactions. One of the challenges in blockchain technology is to ensure the security and availability of funds without relying on a single trusted entity.
Verichains security research into popular open-source t-ECDSA libraries
As part of our ongoing research into threshold ECDSA security, our Security Research team has recently discovered critical key extraction attacks in many popular Threshold Signature Scheme (TSS) implementations that use a Multi-Party Computing (MPC) protocol. Our team is committed to responsible vulnerability disclosure and has taken careful and considered steps when disclosing these attacks, especially given the wide range of impacted projects and significant user funds at risk.
Read our announcement here:
It is important to note that our inclusion of names such as BNY Mellon, Revolut, ING, Binance, Fireblocks, and Coinbase, does not imply that they are vulnerable to our attacks. These institutions, along with many others, have implemented MPC protocols for Threshold Signature Scheme.
Despite multiple security audits, our research has found that nearly all threshold ECDSA-based TSS implementations, including popular open-source libraries in Golang and Rust, are vulnerable to key extraction attacks. We have built working proof-of-concept (PoC) attacks demonstrating full private key extraction by a single malicious party in 1-2 signing ceremonies on various popular wallets, non-custodial key infrastructure, and cross-chain asset management protocols. The attack leaves no trace and appears innocent to the other parties.
Responsible Vulnerability Disclosure
Given the confirmation of multiple vendors impacted, and as part of our commitment to responsible vulnerability disclosure, our Security Research team has followed a deliberate and careful disclosure process.
Our first task was to notify vendors and projects we confirmed are affected by our attacks with Proofs-of-Concept (PoC) of their open-source implementations. We have done this through this week, and we plan to wait for these vendors and projects to fix the issues before we proceed to the second wave of disclosure, in which we will share our attacks with other vendors, including closed-source proprietary software vendors which we do not know if they are vulnerable or not.
As there are numerous open-source MPC libraries and products implementing t-ECDSA, Verichains Security Research team cannot possibly know them all. Therefore, in addition to notifying known affected projects and vendors, we have also issued a press release to inform everyone using t-ECDSA about the issue and offer the opportunity to contact us for more information.
We take the security and safety of all vendors and users seriously and encourage anyone using t-ECDSA to reach out to us for additional details.
Example of how we have previously worked with an affected vendor (different attack) and documented our discovery and disclosure in VSA-2022-120:
Results from our PR can be seen here:
https://finance.yahoo.com/news/verichains-discovers-critical-key-extraction-145051083.html
https://coinmarketcap.com/community/articles/642186472d80720f9caa3bbe/
Due to the generic nature of these attacks, and their impacts are confirmed to be widespread, Verichains requires all projects and vendors to sign a strict NDA before we can disclose our findings to prevent potential leakage and/or misuse of the attacks.
To ensure that all affected parties have enough time to remediate the issues, we plan to wait for a period of 90-120 days before sharing the paper publicly. During this period, we will continue to work with the affected vendors and provide support to ensure that they can implement the necessary fixes to protect their users.
Last Week’s Incidents
🚨Project: Indexed Finance
⛓️Chain: Ethereum
💥Type: Flashloan Attack
💸Loss amount: $15,000
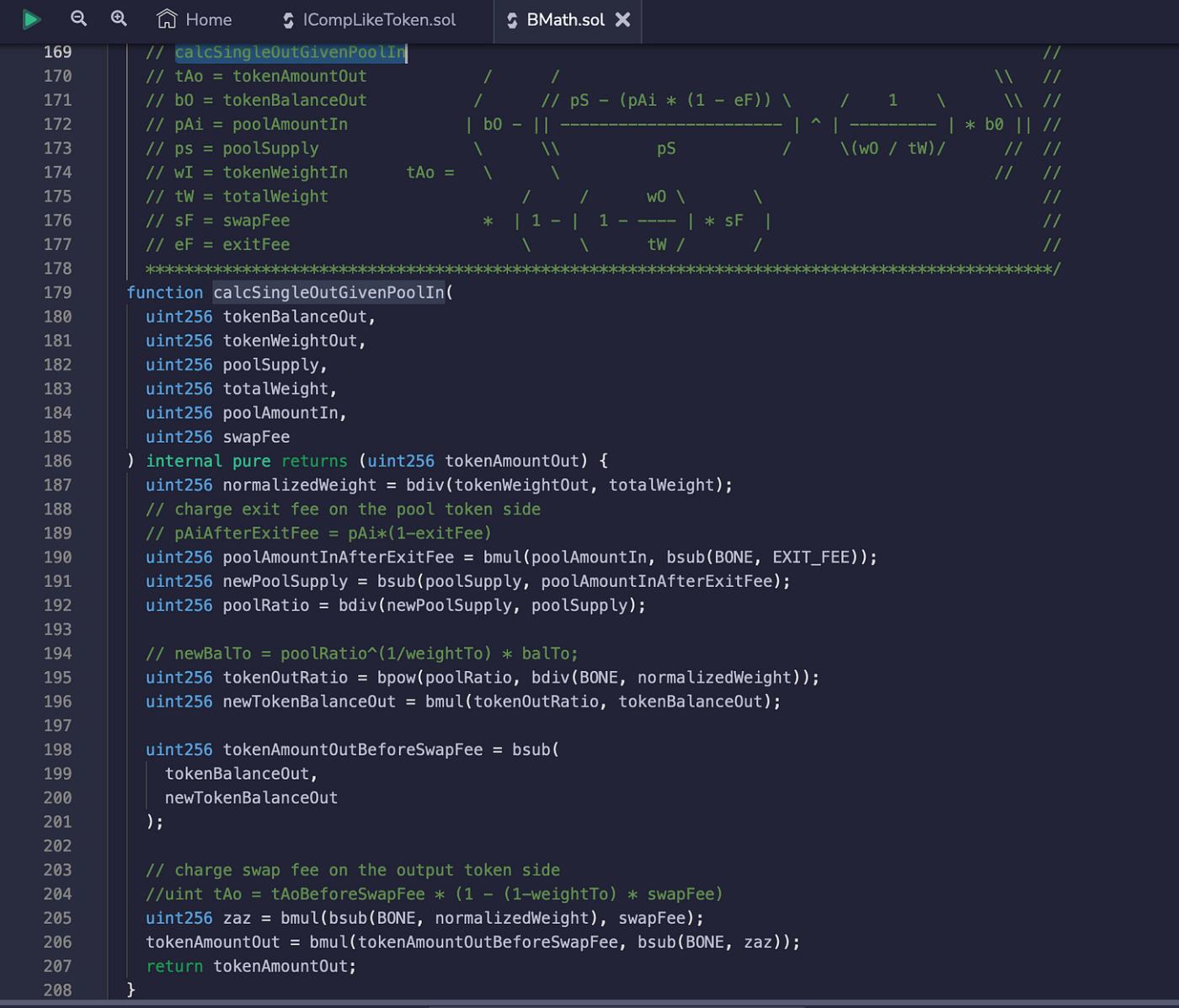
Last week, an attacker got away with $15,000 from exploiting Indexed Finance, a DeFi project. The attack occurred due to an error in the "calcSingleOutGivenPoolIn()" function, which resulted in the incorrect calculation of the tokenAmountOut value.
🚨Project: N/A
⛓️Chain: Polygon
💥Type: Improper Access Control
💸Loss amount: $70,000
An un-named project on Polygon was hacked for $70,000. The exploit was caused by a deficiency in access control within the "daoChange()" function of the target contract (0x9083430f54f100b1b2f20320e5e8484ce319cb97). By changing the DAO address to the attacker's exploit contract, they were able to withdraw all funds from the target contract, which included USDT, WMATIC, and TNDR.
🚨Project: ASKACR
⛓️Chain: BSC
💥Type: Transfer Zero
💸Loss amount: ~$28,000
A token called $ASKACR lost roughly $28,000 from a hack last week where the attacker was able to exploit a vulnerability in the reward distribution mechanism during function transfers. The flaw occurs due to improper verification of transfer amounts, allowing attackers to claim more rewards from LP holders by repeatedly transferring 0 $ASKACR tokens using LP tokens resulting in a considerable amount of ill-gotten gains.
🚨Project: Big Finance
⛓️Chain: BSC
💥Type: Deflationary Token
💸Loss amount: $30,000
In another attack involving a deflationary token a DeFi project called Big Finance was hacked for $30,000. The attacker utilizes a flashloan and burn function to manipulate tTotal, resulting in a significant reduction in the pair's balance. This manipulation allows the attacker to swap out USDT for the pair's now-minimal balance.
🚨Project: $DBW
⛓️Chain: BSC
💥Type: Business Logic Flaw
💸Loss amount: $24,000
A business logic flaw cost a token project $24,000. The root cause of the issue is that dividend awards are calculated based on the percentage of LP owned by the user at the time, without considering any subsequent dividends after the LP transfer.