In this installment of Verichains Weekly Digest, we will walk readers through the process of Verichains Responsible Vulnerability Disclosure as well as it's value proposition. For last week’s incidents, the DeFi market was hacked for over $20 million.
Verichains Security Advisory
As Verichain's wait period is in effect for affected vendors to remedy their products from our key extraction attacks disclosure, it is crucial to understand Verichains' standard procedure for handling vulnerability disclosures. When a vulnerability is discovered, our security researchers reproduce it in a controlled environment (a proof of concept, or PoC), this enables the researchers to assess the severity and level of impact of the vulnerability without affecting the product.
Once the vulnerability is confirmed via the PoC, we will prepare and deliver a ‘vulnerability disclosure’ notification to the affected vendor. Vendors may receive the disclosures through a few different channels, such as a bug-bounty program, a dedicated vulnerability disclosure program/policy, or directly to their security inbox. Verichains also takes an additional security step, by encrypting the PoC in our transmission and this is to prevent unauthorized parties from viewing the vulnerability. Furthermore, Verichains maintains confidentiality and does not share our findings, including the PoC, with any third parties. All communication between us and the affected vendor is privileged to ensure the security of their vulnerable product.
Upon receiving the disclosure, the affected vendor acknowledges the notification and begins their internal review and verification of PoC. Simultaneously, the vendor can initiate their existing security procedures to ensure the proper management of the disclosed vulnerability.
The value proposition for the vendor is clear, they were made aware of a vulnerability in their product, before any exploitation can take place. Vendors can work with Verichains to receive additional information and assistance in fixing the vulnerability or perform the fix themselves if they have the technical capability. By working with the Verichains, the vendor can quickly patch the vulnerability, and to mitigate against the potential loss of funds, business disruption, or reputational damage resulting from exploitation.
During this time, Verichains 120-day waiting period is in affect, allow the for the vendor plenty of time to patch the vulnerability. After the vendor has patched the vulnerability and/or the waiting period has lapsed, Verichains will publish the details of the vulnerability in a public disclosure through our Security Advisory, which you can reference here:
To discover how Verichains can help your security efforts, contact us via info@verichains.io
Last Week’s Incidents
🚨Project: MEV bot
⛓️Chain: Ethereum
💥Type: Front-run, sandwich attack
💸Loss amount: $20 million
Similar to the SafeMoon hack in last digest, another MEV bot was hacked for a monumental $20 million in just one block. The attack was seemingly carried out by a validator who inserted their transaction, allowing them to steal funds from the MEV bot that was trying to front-run. Front-running involves placing a transaction ahead of others to gain an advantage and exploit price differences.
🚨Project: Sushi Swap
⛓️Chain: Ethereum, Polygon, Arbitrum, Avalanche, BSC, etc.
💥Type: Access Control
💸Loss amount: $3.3 million
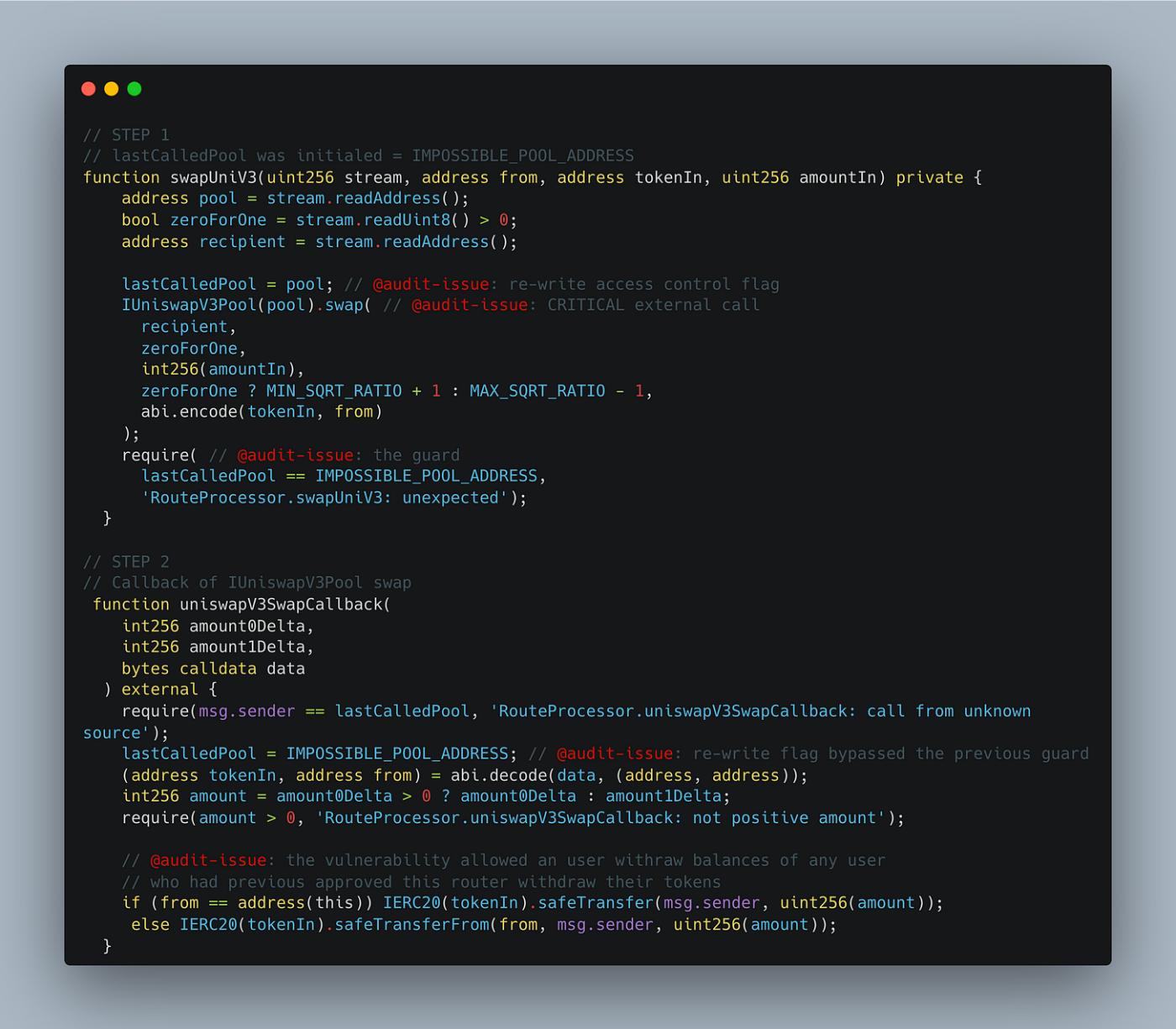
Last week, the DeFi market suffered 2 major hacks with the first one costing $3.3 million on Sushi Swap, a well-known decentralized exchange. The vulnerability was found in the RouteProcessor2 contract, which includes a function called processRoute that handles off-chain generated routes for swapping tokens.
The vulnerability was caused by a lack of proper access control in the processRoute function, allowing a malicious user to exploit it. The attacker was able to swap any token through the router by calling the processRoute function and passing in a victim's address. As a result, the balances of the victim's tokens, specifically the BUZZ token, were transferred to the hacker's address, effectively draining the victim's account.
This unauthorized access and transfer of tokens by the hacker was made possible due to the lack of proper access controls in the vulnerable function, allowing them to exploit the approval granted by users when initiating swaps, and manipulate the balances of the victim's tokens.
🚨Project: Sentiment
⛓️Chain: Arbitrum
💥Type: Reentrancy
💸Loss amount: ~$1 million
Another $1 million was also stolen in a DeFi protocol called Sentiment in an attack that exploited the view re-entrancy bug. The attackers took a flashloan, changed rates, and called the "exitPool" function to execute malicious code before pool balances were updated. This allowed them to overprice their collateral and borrow and withdraw more assets from the Sentiment pool than they should have been able to. By manipulating the values of the balances and total supply in the Sentiment pool, the attacker executed a collateral manipulation attack, stealing money from the protocol.
In the latest update, Sentiment had successfully negotiated with the attacker to return 90% of the hacked fund, keeping 10% as a white-hat fee.
https://twitter.com/sentimentxyz/status/1643779654141251584?s=20