In this week’s digest, Verichains investigation reveals the root cause of the recent $1.8 million Merlin DEX rug pull, the event has put the spotlight back onto the security vendor and the careful consideration that project owners should take when deciding their security partner.
For this week's incidents, the DeFi market lost over $1.9 million in hacks.
How it Unfolds
On April 26th, 2023, Wu Blockchain reported on an alleged hack of a zkSync decentralized exchange (DEX) called Merlin, citing Certik as the DEX’s security auditor.
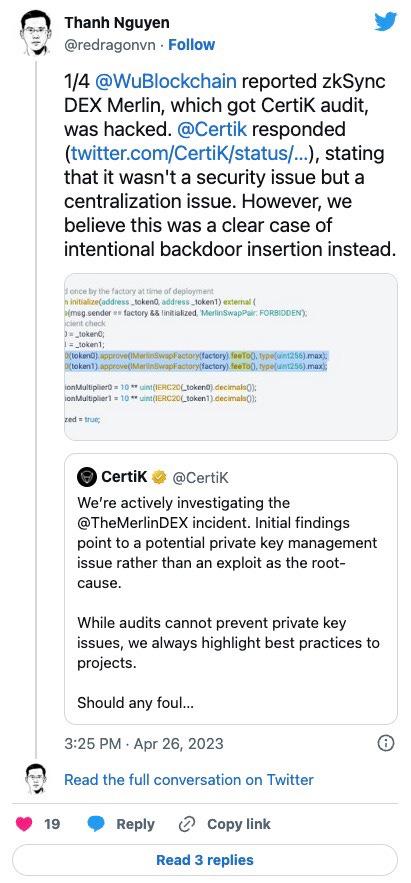
In response, the auditor suggested the incident was caused by a private key management issue instead of a security exploit. Merlin promptly acknowledged the incident on Twitter, urging users to revoke connected site access on their wallets/sign permission.
As the situation was developing and more information was being shared, the crypto community at large remains unclear as to what has happened and started to speculate on the root cause of the incident.
Verichains Independently Investigate
Led by our co-founder Thanh Nguyen, Verichains security researchers immediately picked up on this situation and opened an independent investigation to determine the root cause.
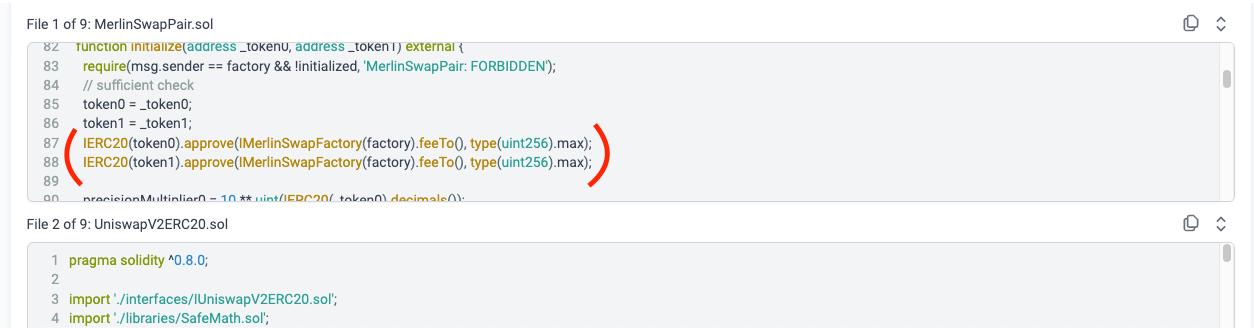
Before discussing the result, it is necessary to understand the architecture of the DEX. Merlin DEX is a fork of the Uniswapv2 protocol where each LP pair is an ERC20 token that holds assets for the AMM pool. In the UniswapV2 protocol, the pair will mint a fee to the Factory fee receiver each time the swap function is executed.
Our investigation of Merlin DEX reveals a pair of “backdoor” codes at L87-88 that allows the feeTo of MerlinFactory to transfer all assets in the pair, in addition to the fee in the swap function. In our assessment, there is no use case that requires the approval of these codes and they are a clear security risk.
Generally, a backdoor vulnerability can be intentionally or accidentally implemented into one’s code, used to gain unauthorized access, manipulate the blockchain, or in this case, steal funds.
The findings were shared on our co-founder’s Twitter account which went viral and was picked up by various news outlets:
Wu Blockchain: https://twitter.com/WuBlockchain/status/1651153245363109889?s=20
Cointelegraph: https://cointelegraph.com/news/certik-zksync-to-launch-compensation-plan-for-2m-merlin-dex-exploit
The Aftermath
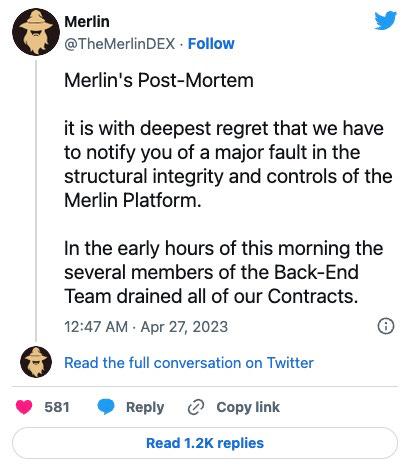
As news about the backdoor raised more attention from the crypto community, Merlin DEX tweeted a post-mortem 12 hours after the incident, acknowledging the exploit and alleging that 3 members of their back-end team had fraudulently modified the code to include the backdoor and use it to drain all of the DEX’s contract.
Merlin DEX also mentioned their security vendor's “oversight on the overarching power the owner had of the pools.” The situation regarding Merlin and Certik’s plan to compensate affected victims is still developing.
This incident should remind projects and crypto users the importance of performing due diligence when it comes to vetting a security vendor.
At Verichains, we stand as an independent security firm that aims to promote truth and transparency in the crypto market.
Last Week’s Incidents
🚨Project: AutoDonateUkraine
⛓️Chain: BSC
💥Type: Reflection Token
💸Loss amount: $7,000
A token project called AutoDonateUkraine suffered a flashloan attack for $7,000. The attacker utilized the "deliver" function to increase the amount of $ADU in the pair and then withdrew the excess $ADU using the "skim" function. By repeating this operation multiple times, the attacker was able to unbalance the price in the pair and profit 22 $WBNB from the pair.
🚨Project: Never Fall
⛓️Chain: BSC
💥Type: Price Manipulation
💸Loss amount: $74,000
A project called Never Fall on BSC also suffered a flashloan attack, resulting in a loss of 74,000. The attack involved a flashloan of 1.6M BUSD, with 200K BUSD used to purchase 75.5M Never Fall tokens through the buy function in the Never Fall contract. The buy function added liquidity with 90% BUSD deposited by the user and Never Fall in the contract, and swapped the remaining BUSD in the pair. The remaining 1.4M BUSD was swapped for Never Fall in the BUSD-Never Fall pool. The attacker then sold the held Never Fall via the sell function, which sent the user the added BUSD after liquidity was removed from the contract.