In this week’s Digest, Verichains discusses Ledger’s recent controversies in relation to its seed phrase recovery feature.
In incident news, the DeFi market was hacked for $1 million
Ledger Recover Discussion
On May 16th, Ledger unveiled its latest feature, Ledger Recover, sparking controversy and misunderstandings around the concept of "trustlessness" in hardware wallets and security concerns associated with the recovery feature. Verichains aims to provide market clarity on trustlessness in hardware wallets and the security implications of introducing a feature that grants direct access to your private keys.
Read the full article here: https://blog.verichains.io/p/ledger-the-trustless-discussion
Last Week’s Incidents
🚨Project: LunaFi
⛓️Chain: Polygon
💥Type: Business Logic Flaw
💸Loss amount: ~$36,000
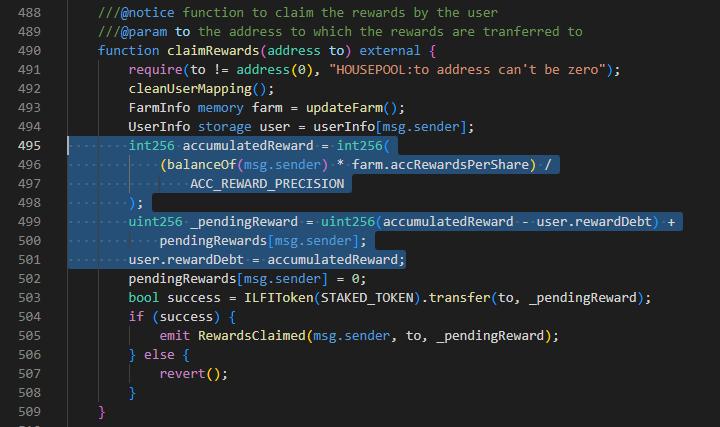
Last week, a Web3 betting platform called LunaFi was hacked for ~$36,000 due to a vulnerability in the code’s "claimRewards" function. Attackers are taking advantage of the lack of a time lock on staked tokens by calling the function, creating a new contract, and transferring tokens to continue claiming rewards. This allows them to accumulate rewards without any time restrictions. Implementing a time lock mechanism on staked tokens can address this issue.
At the time of writing, the project had acknowledged the hack, take full responsibility, and is working closely with Hackenclub to chart the next steps.
🚨Project: LOCALTRADERSCL
⛓️Chain: BSC
💥Type: Access Control
💸Loss amount: ~$118,000
A government-registered P2P exchange in Chile was exploited for approximately $118,000 due to a vulnerability lies in the function with the address 0xb5863c10, which does not have a permission check in place. This means that anyone can call this function and modify the owner of the contract.
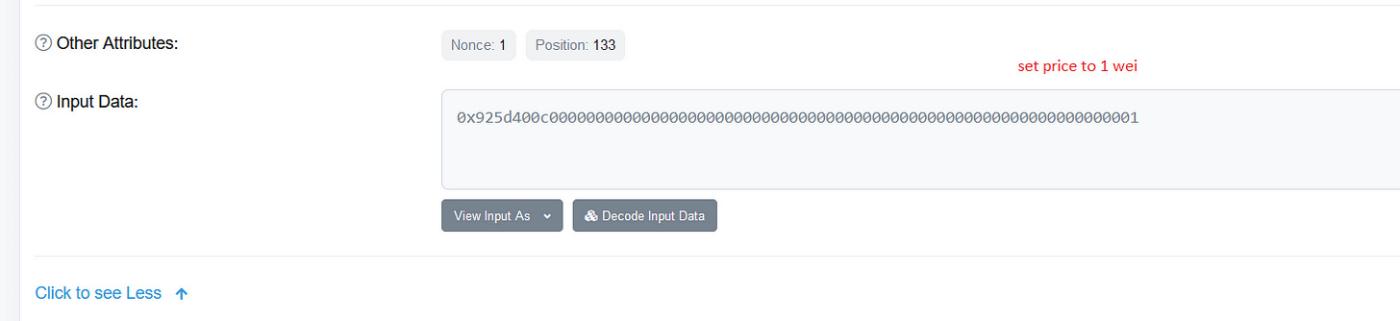
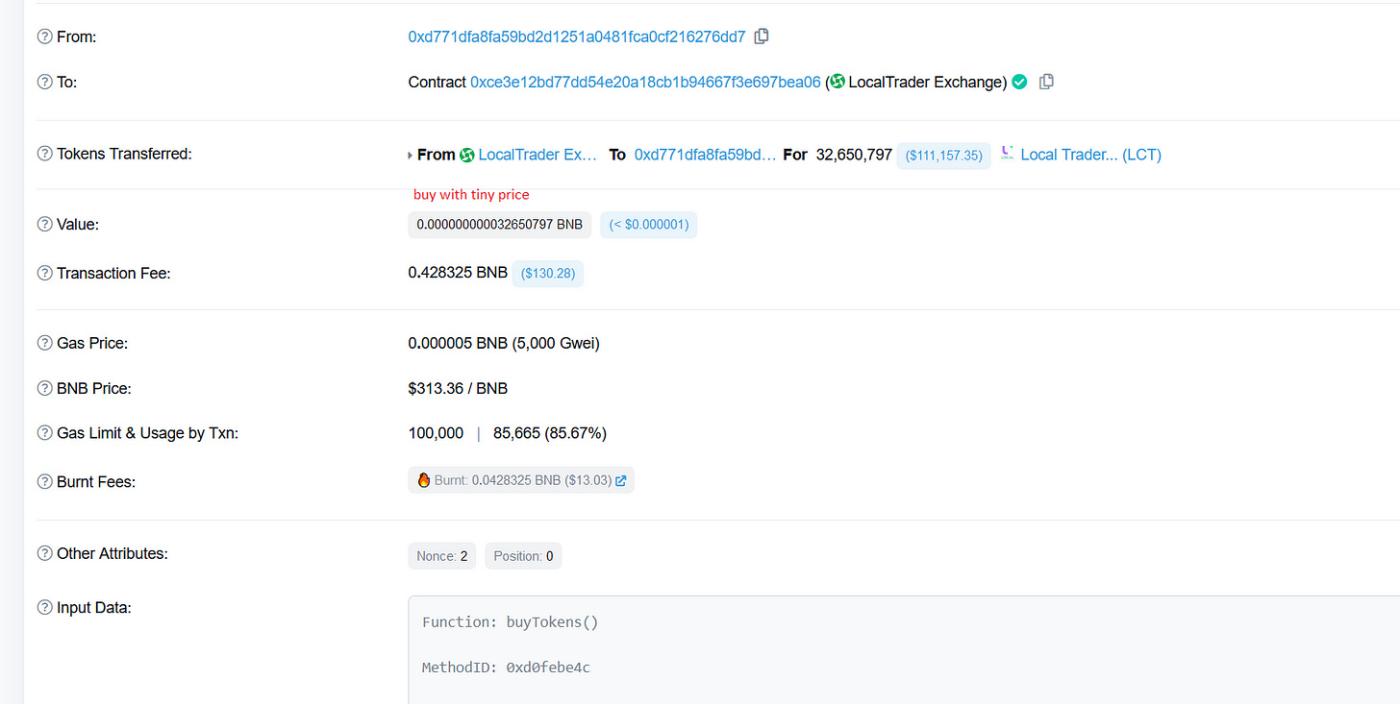
An attacker took advantage of this vulnerability by calling the 0xb5863c10 function and setting themselves as the owner of the contract. Once they became the owner, they proceeded to use the 0x925d400c function to modify the price to 1. By manipulating the price, the attacker aimed to buy $LCT tokens at a low price.
With the price set to 1, the attacker likely bought a significant amount of $LCT tokens at a reduced price. After acquiring these tokens, they then sold them at a higher price, making a profit from the price discrepancy. The platform had since patched the vulnerability in a newly deployed staking contract.
🚨Project: CSToken
⛓️Chain: BSC
💥Type: Outdated Global Variable
💸Loss amount: $714,000
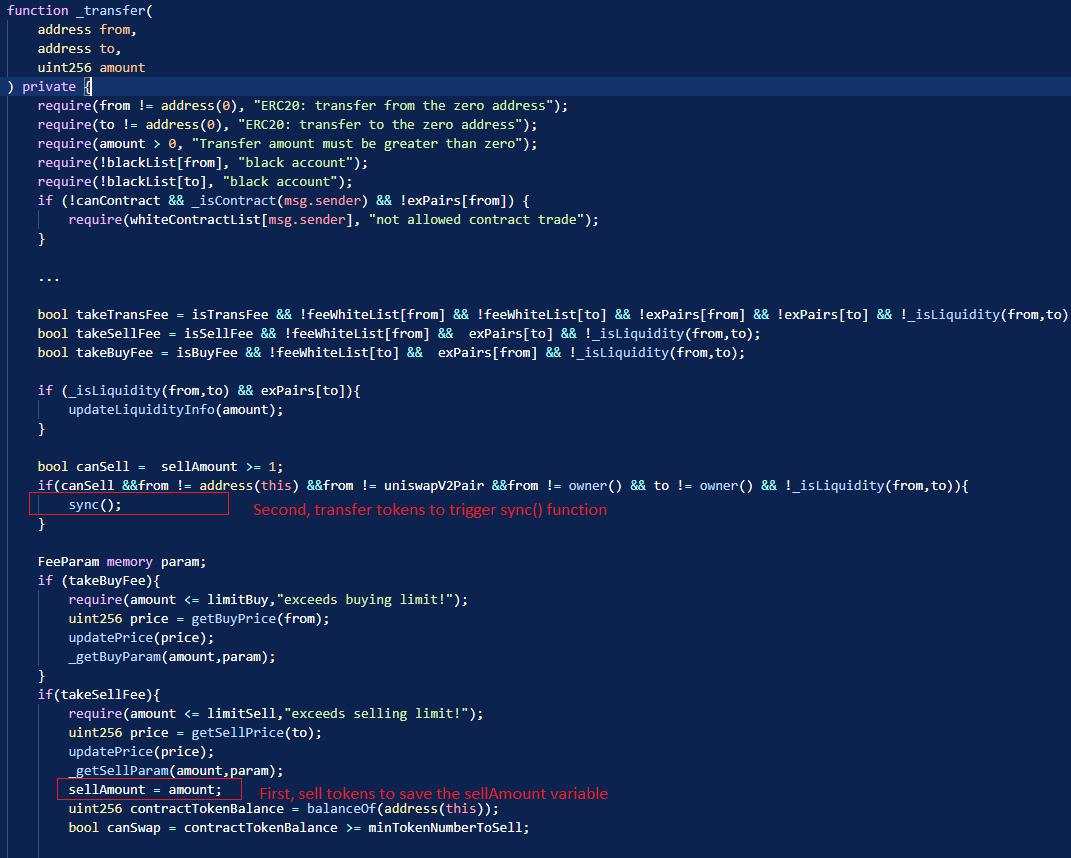
During a recent attack, the $CS token on BSC suffered a hack resulting in a loss of $714,000. The attack was made possible by exploiting a vulnerability related to the sellAmount global variable within the _transfer function. This variable was not promptly updated, allowing the attacker to manipulate the token contract.
By taking advantage of this vulnerability, the attacker engaged in a technique where they burned $CS tokens in pairs. This action artificially inflated the price of $CS tokens during exchanges. As a result, the attacker benefits from the inflated price and profits from the manipulated market conditions.
🚨Project: Tornado Cash Governance
⛓️Chain: ETH
💥Type: Malicious Governance Proposal
💸Loss amount: N/A
The Tornado Governance contract experienced an exploit through a malicious proposal attack. Here's a simplified breakdown of what happened:
1. The attacker (address: 0x592340957ebc9e4afb0e9af221d06fdddf789de9) deployed a contract called contract1 at address 0x7dc86183274b28e9f1a100a0152dac975361353d using the create2 opcode
2. Within the same transaction (available here), contract1 deployed another contract named contract2 using the create opcode.
3. The attacker then submitted contract2 as a proposal for the Tornado Governance contract, as seen in the transaction here.
4. Both contract1 and contract2 contained a selfdestruct function. However, normal users who voted for the contract2 proposal didn't realize that the proposal contract code included a selfdestruct function.
5. Once the attacker collected enough votes, they destroyed both contract1 and contract2. Afterward, they re-deployed contract2 with a modified malicious code that set the locked balance of addresses controlled by the attacker to 10,000.
6. By executing the malicious proposal, the attacker was able to withdraw TORN tokens from the Tornado Governance Vault to their own addresses using the unlock function. This can be observed in the transaction here.
🚨Project: $GPT
⛓️Chain: BSC
💥Type: Token Fee Mechanism Manipulation
💸Loss amount: ~$155,000
A meme token called $GPT was hacked for around $155,000 due to a vulnerability in the burn feature in the GPT token. This exploitation occurred due to a contract miscalculation, which resulted in the manipulation of the price of an LP (Liquidity Pool).
The attacker took advantage of this vulnerability by repeatedly burning tokens that were meant to be added to the LP Pool. By doing so, they caused significant fluctuations in the price of the token within the LP Pool.