Written by: shingle, Frank, Foresight News
Latest news: Paradigm researcher samczsun tweeted again that the Twitter vulnerability has been fixed. The technical summary is that reflected XSS and CORS/CSP bypass in the Twitter subdomain allow arbitrary requests to the Twitter API as a locally authenticated user.
The following is the original text: This morning, Chaofan Shou, a doctoral candidate at the University of California, Berkeley, tweeted that he discovered an unpatched vulnerability in Twitter. Paradigm researcher samczsun then quoted Chaofan Shou as saying that if a user clicks on a link prepared by a hacker, the hacker will be able to fully access you. Twitter account, including the ability to tweet, retweet, like, block, etc.
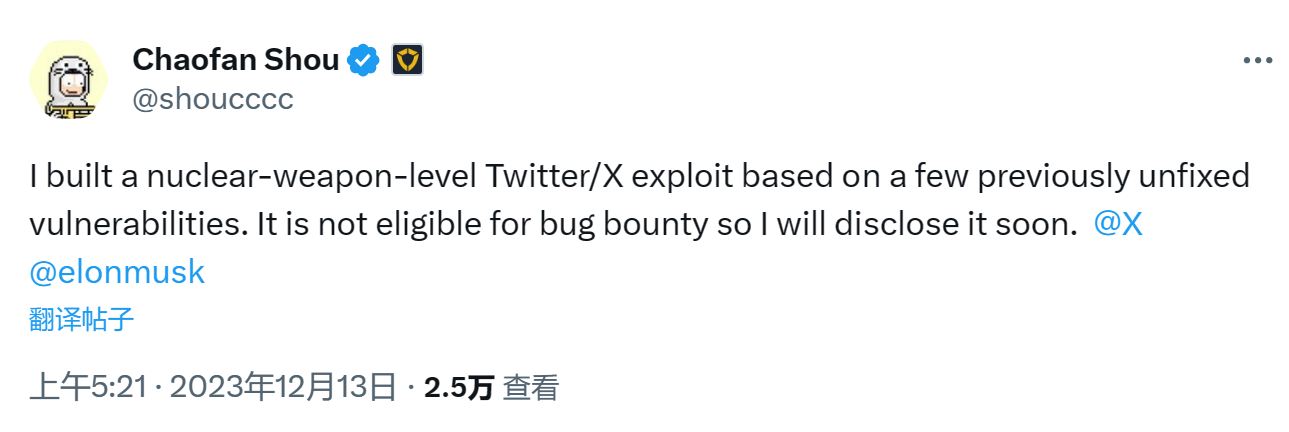
As of the time of publication, Twitter has not yet issued an official statement on this. Foresight News briefly analyzes the attack logic of this vulnerability, as well as the security instructions and prevention methods for ordinary users.
Vulnerability attack logic
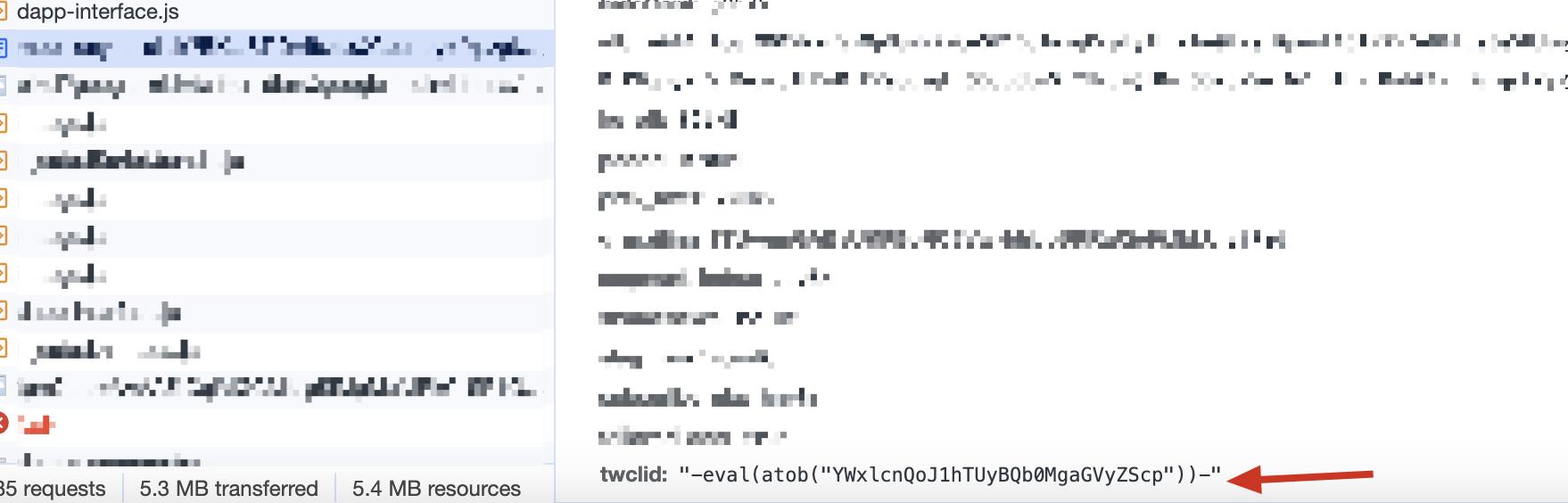
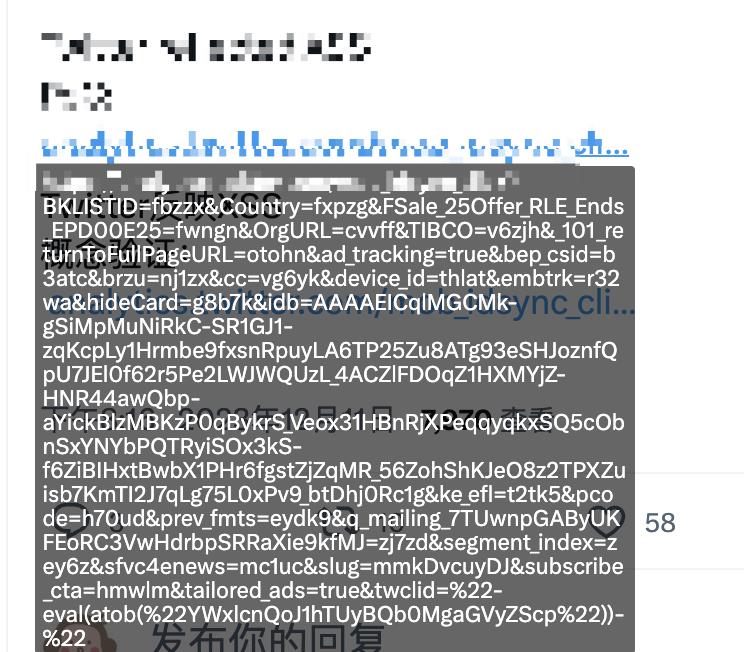
The Twitter vulnerability that was exposed this time is an XSS attack, which is a code injection attack - the attacker can construct a website link with malicious code in advance, and the malicious code will be executed on the web page after the user clicks it .
For example, in the example given, the malicious code is base64 encoded and executed, and the actual execution is alert('XSS PoC here').
When a user accesses this malicious link, the webpage will execute this code and pop up this string:
How can users protect themselves?
Because this kind of construction code needs to be placed in the URL, it will cause the length of the malicious link to be very long.
Therefore, when users encounter extremely long links while brushing up, do not click on them! Or if you really want to see it, you can copy it and open the browser in incognito mode to view it .
In short, do not click on unknown long links on the browser logged into your Twitter account.
If you are unfortunately caught, just change your Twitter password immediately. The most valuable part of this attack is to steal your Twitter auth_token. Changing the password will cause the previous auth_token to become invalid.