The total losses caused by security incidents in the first quarter of 2024 reached 462 million US dollars. Factors such as the rise in currency prices this quarter had a certain impact on the increase in the total amount, but overall, the security situation of Web3 is not optimistic.
Author: SharkTeam
Cover: Photo by Markus Spiske on Unsplash
I. Overview
In the first quarter of 2024, hacker attacks, Rugpull scams, phishing attacks and other malicious behaviors caused a total loss of US$462 million, an increase of approximately 18.02% year-on-year compared with the first quarter of 2023 (approximately US$383 million). This report aims to organize and analyze the security status, major events and security trends of the global Web3 industry in the first quarter of 2024, provide readers with useful information and new ideas, and contribute to promoting the safe and healthy development of Web3.
2. Security Incident Analysis
According to data from SharkTeam's on-chain security analysis platform ChainAegis, a total of 280 security incidents occurred in the Web3 field in the first quarter of 2024 (as shown in Figure 1), with a cumulative loss of more than US$462 million (as shown in Figure 2). Compared with the same period last year, the frequency of security incidents increased by approximately 32.70%, and the amount of losses increased by approximately 20.65%.
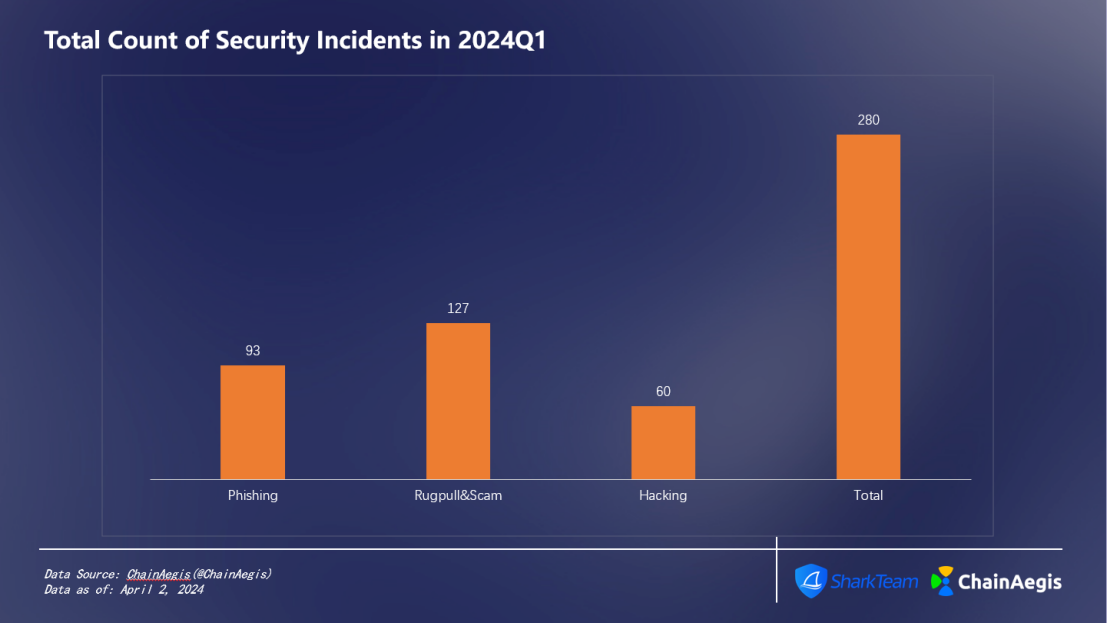
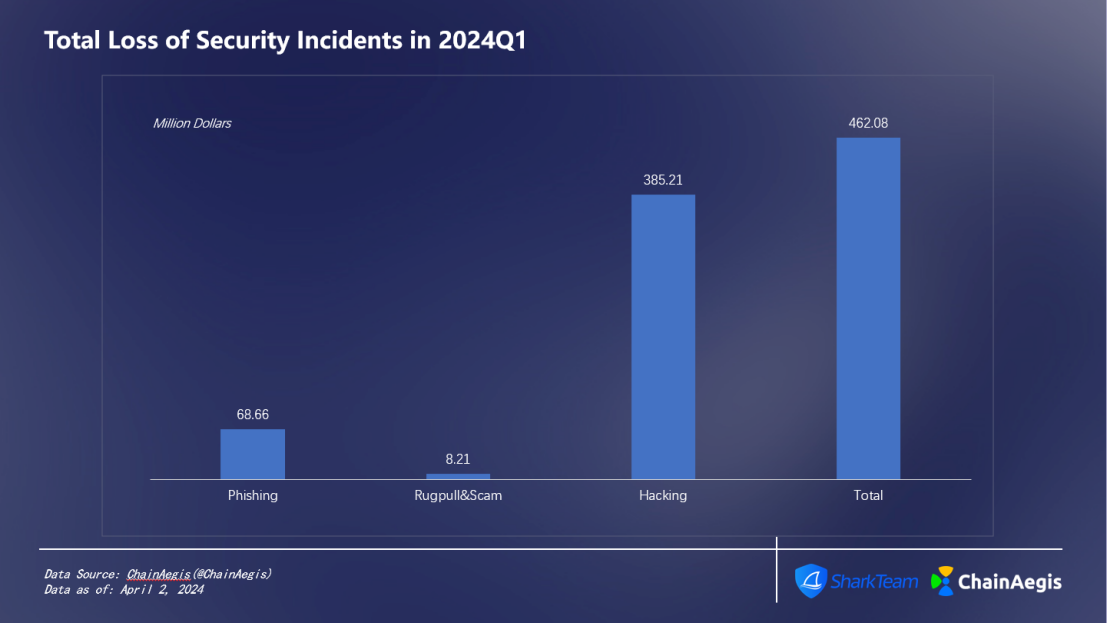
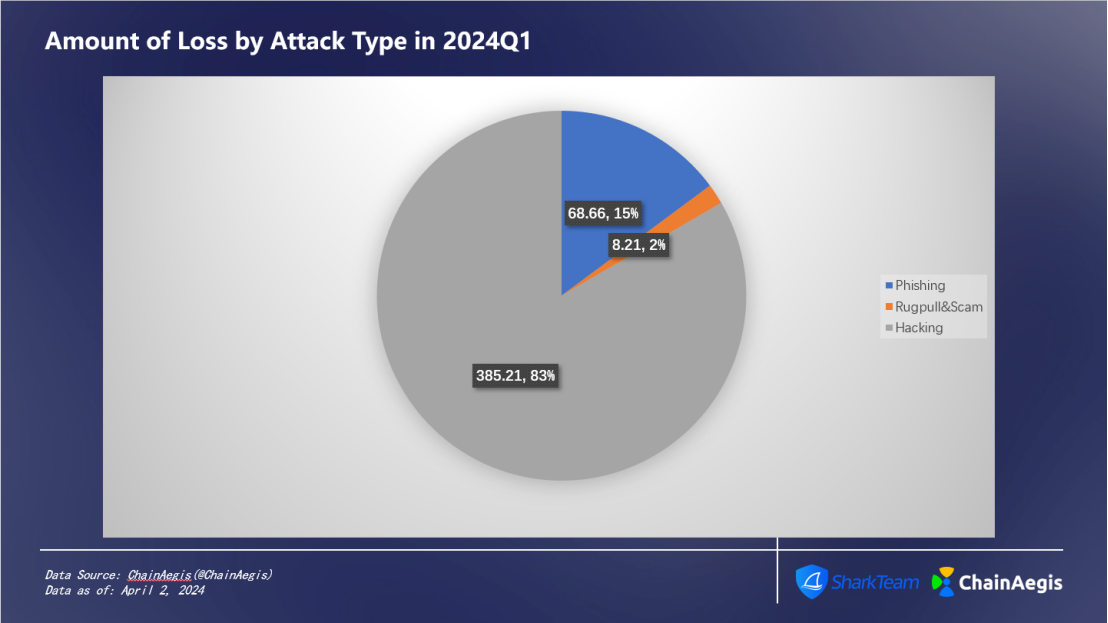
There were 60 hacker attacks in Q1 2024, an increase of 140% compared with Q1 2023. The amount of losses reached US$385 million, accounting for 83% (as shown in Figure 3), an increase of 6.35% year-on-year compared with Q1 2023 (US$362 million).
There were 127 rug pulls, a 323.33% increase from Q1 2023 (30 cases), but the amount of losses fell by 59.44% to US$8.21 million, accounting for 2% of the total losses in Q1.
There were 93 phishing attacks in total in Q1, an increase year-on-year, with losses of approximately US$68.66 million, accounting for approximately 15%.

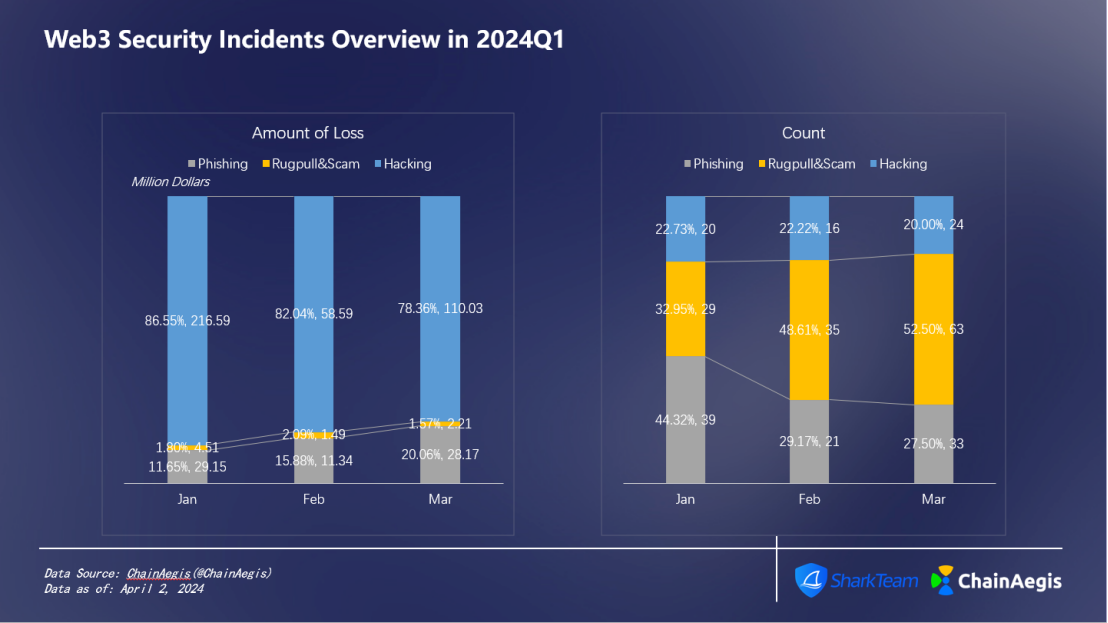
Looking at Q1 by month (as shown in Figure 5), the loss in January was the most serious, exceeding $250 million, much higher than February (71.42 million) and March (140 million). Among them, there were 88 security incidents in January, slightly higher than 72 in February and slightly lower than 120 in March. It can be seen that the loss amount of a single security incident in January was the highest. The attack method that caused serious losses in January was hacker attacks, with a total of 20 hacker attacks, causing losses of $217 million. At the same time, phishing attacks also occurred frequently in January, with a total of 39 phishing attacks, but the loss amount was relatively the lowest, totaling $29.15 million. The overall frequency of security incidents and the amount of losses in February were both at a lower level than those in January and March.
2.1 Hacker Attacks
There were 60 hacker attacks in the first quarter, with a total loss of $385 million. The most serious loss was $217 million in January. The main reason was that there were two large-scale financial losses in January.
(1) On January 1, 2024, the cross-chain bridge project Orbit Chain suffered a cyber attack, resulting in the theft of approximately $81.5 million worth of cryptocurrency. The incident involved five separate transactions, each pointing to a different wallet address. The unauthorized flow of funds included $50 million in stablecoins (including $30 million in USDT, $10 million in DAI, and $10 million in USDC), 231 wBTC worth approximately $10 million, and 9,500 Ethereum worth approximately $21.5 million.
(2) On January 31, 2024, four wallets of Chris Larsen, co-founder of Ripple, were attacked, and a total of 237 million XRP were stolen, equivalent to approximately US$112.5 million. ChainAegis on-chain analysis shows that the stolen funds have been transferred through MEXC, Gate, Binance, Kraken, OKX, HTX, HitBTC, etc. This is the largest cryptocurrency theft so far in 2024 and the 20th largest cryptocurrency theft in the crypto world so far. The price of XRP fell by approximately 4.4% within 24 hours of the incident.
2.2 Rug Pull & Scams
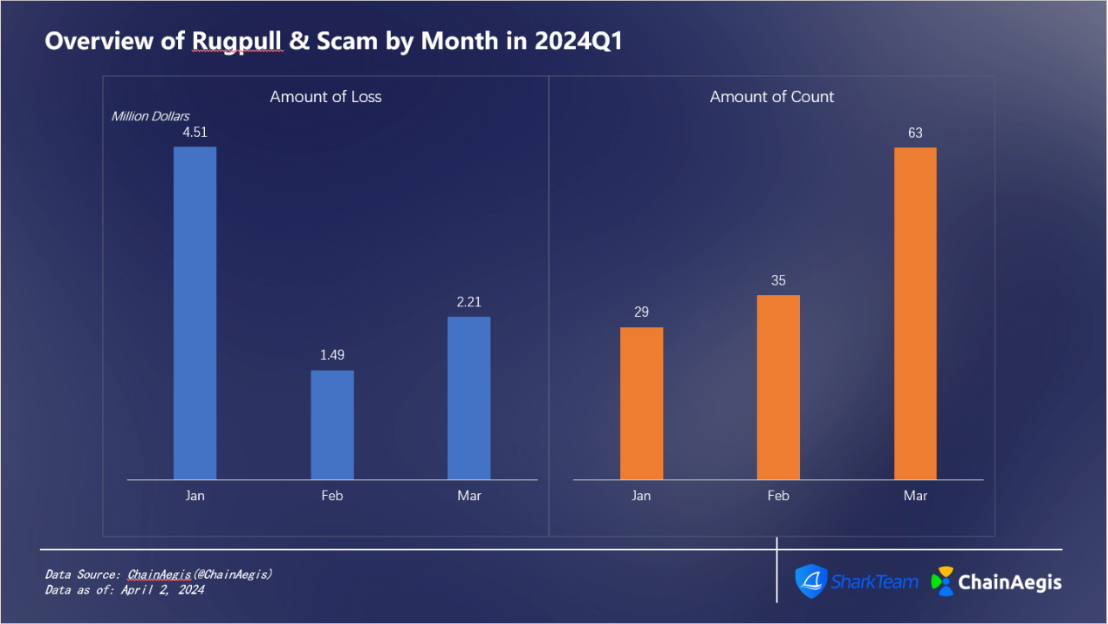
As shown in the following figure (Figure 6), there were 29 Rugpull & Scam incidents in January, which increased month by month, with about 63 incidents in March; the loss in January was about 4.51 million US dollars, and the loss in February was about 1.49 million US dollars. According to ChainAegis analysis, the incidents were concentrated in the mainstream chains Ethereum and BNB Chain, and the frequency of Rug Pull incidents in the BNB Chain project was much higher than that of Ethereum.
In addition, on February 25, RiskOnBlast, a GameFi project of the Blast ecosystem, had a rugpull. According to ChainAegis analysis, RiskOnBlast's address 0x1EeB963133f657Ed3228d04b8CD9a13280EFC558 raised a total of 420 ETH, worth about $1.25 million, from February 22 to 24, but then converted it into DAI and transferred it to deposit addresses of exchanges such as ChangeNOW, MEXC, and Bybit for cash.
2.3 Phishing Attacks
As shown in the following figure (Figure 7), phishing attacks occurred most frequently in January with 39 attacks, resulting in losses of approximately $29.15 million; the lowest frequency occurred in February with 21 attacks, resulting in losses of approximately $11.34 million. SharkTeam reminds everyone that the bull market is active and there are many airdrop opportunities, but everyone should be vigilant to avoid being attacked by active phishing groups such as Angel Drainer and Pink Drainer, and be sure to carefully check the transaction information when transferring and authorizing.

3. Typical Case Analysis
3.1 Contract Precision Calculation Vulnerabilities and Security Suggestions
On January 30, 2024, MIM_SPELL suffered a flash loan attack and lost $6.5 million due to a precision calculation vulnerability. The reason for the attack was that the project's smart contract had a precision vulnerability when calculating loan variables, causing the key variables elastic and base values to be manipulated and unbalanced, resulting in problems in calculating collateral and loan amounts, and ultimately over-borrowing MIM tokens.
In the attacked contract (0x7259e1520), the borrow function and the repay function both round up when calculating the two variables elastic and base.

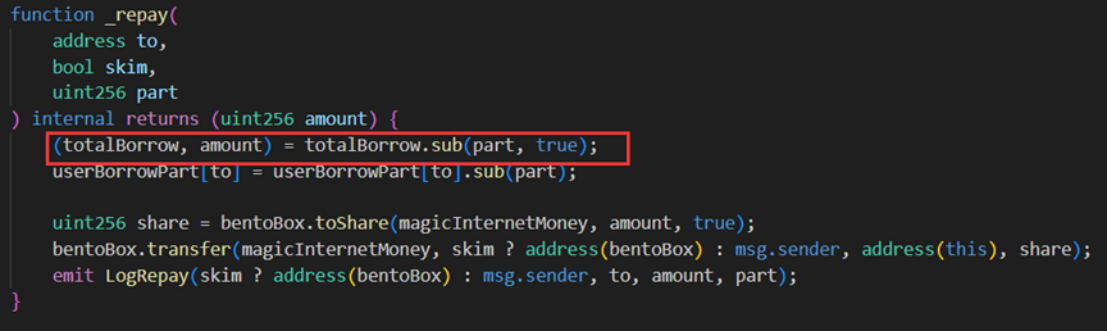

The attacker (0x87F58580) first set the elastic variable and base variable to 0 and 97 respectively by repaying other users' loans.
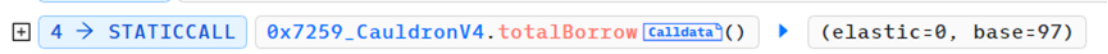
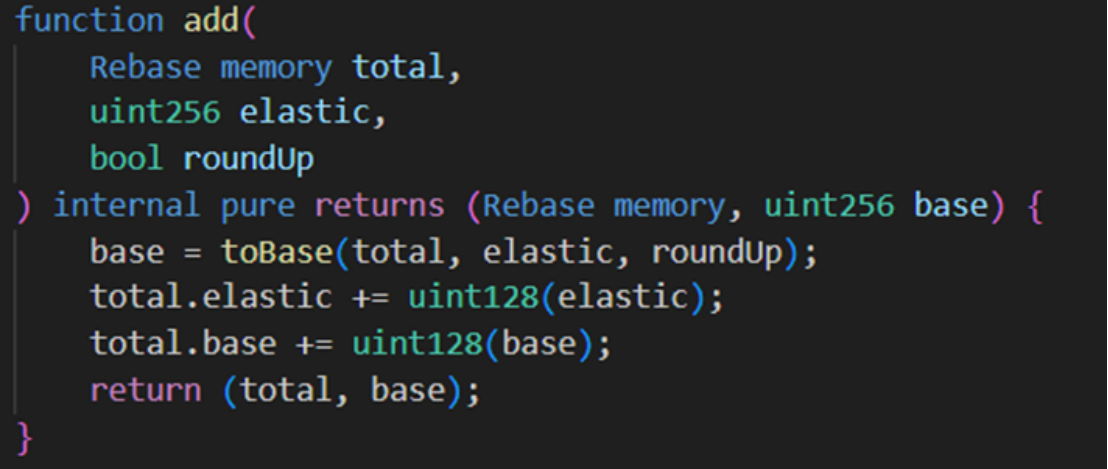
Then the borrow function and the repay function are called continuously with the parameter amount being 1. When the borrow function is called for the first time, since elastic=0, the above if logic will be executed and the function will return to the add function, which will result in elastic=1 and base=98.
The attacker (0x87F58580) calls the borrow function again and passes in 1. Since elastic=1, the else logic is executed and the calculated return value is 98. When returning to the add function, elastic=2 and the base variable is 196.
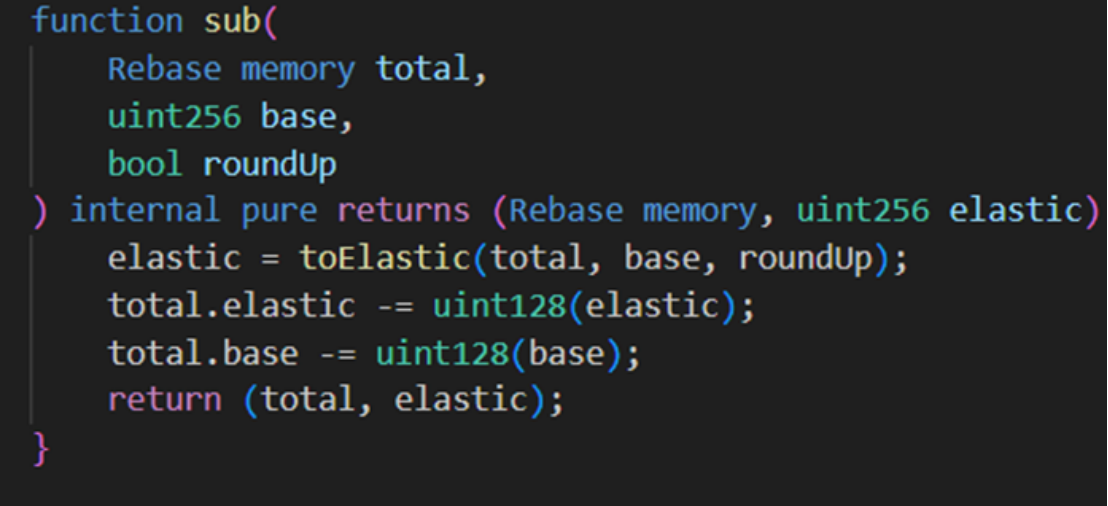
But at this time, the attacker (0x87F58580) calls the repay function and passes in 1. Since elastic=2, the else logic will be executed. The calculated elastic variable is originally 1*2/98 =0, but due to the rounding up step below, the calculated return value is 1. Therefore, when returning to the sub function, the elastic variable becomes 1 again, and the base variable is 195.
It can be seen that after a borrow-repay cycle, the elastic variable remains unchanged while the base variable nearly doubles. Exploiting this vulnerability, the hacker frequently loops the borrow-repay function and finally calls repay again, eventually making elastic=0 base = 120080183810681886665215049728.

When the ratio between elastic and Base variables is seriously unbalanced, the attacker (0x87F58580) can borrow a large number of MIM tokens by adding a very small amount of collateral to complete the attack.

3.2 DeGame phishing attack and Pink Drainer Fraud Gang
In March 2024, a Web3 user unknowingly clicked on a phishing link posted by the hacked DeGame Official Twitter and suffered losses.
Afterwards, the user mistakenly believed that DeGame had embezzled money during the process and disclosed the incident on Twitter. A number of KOLs, media and a considerable number of users continued to spread the matter without knowing it, which had a great impact on DeGame's brand image and platform reputation.
After the incident, DeGame launched an emergency plan to help the victimized users try to recover their assets. The DeGame phishing attack incident was roughly as follows:
(1) Between 4:00 AM and 9:30 AM on March 14, the DeGame official account X (@degame_l2y) sent 4 airdrop tweets. The airdrop links in the tweets were all phishing websites that imitated the official DeGame website. A user reported that he lost about 57 PufETH after clicking on the airdrop link.
(2) DeGame’s official Twitter operator discovered the phishing link on the platform after 9:30 AM and deleted it. At the same time, DeGame synchronized this news to all users through official social media and communities, and issued a warning announcement.
(3) During the abnormal time period of the DeGame official Twitter account, the victim browsed the phishing website link and the description text posted by the attacker. He unknowingly thought that the link was indeed a token airdrop event organized by DeGame and other project parties. After clicking the link, he followed the preset prompts of the attacker and lost his assets.
(4) After the user clicks on the phishing website to connect to the wallet, the website will automatically detect whether there are assets in the wallet address. If there are assets, the Permit Token Approval transaction signature will pop up directly. Unlike conventional transaction signatures, this signature is not on the chain at all, is completely anonymous, and is likely to be used for improper purposes. In addition, users do not need prior authorization and can interact with the application contract by attaching an authorization signature (Permit).
(5) In this theft, the phishing hacker obtained the Permit Token Approval transaction signature of the stolen user authorizing the phishing contract address 0xd560b5325d6669aab86f6d42e156133c534cde90, and submitted Permit in the attack transaction to call Approve to obtain token authorization and then transferred the stolen funds.
(6) The provider of the phishing tools is the hacker fraud group Pink Drainer. Pink Drainer is a malware-as-a-Service (MaaS) that allows attackers to quickly build malicious websites and obtain illegal assets through the malware. In this stolen transaction, about 25% of the stolen funds were transferred to PinkDrainer: Wallet 2, which is the wallet address No. 2 of the phishing group PinkDrainer. It is the automatic share given to PinkDrainer by the phishing implementer after using the phishing tools of the phishing group PinkDrainer.
3.3 Batch Rugpull causes a surge in the number of events
The surge in the number of Rugpull events in 2024 is closely related to the batch creation of Rugpull tokens by the Rugpull factory contract. The SharkTeam security research team conducted a detailed analysis of these Rugpull events. During the analysis, we found that the Rugpull factory contract on the BNB Chain has initiated more than 70 Rugpulls in the past month. Batch Rugpull events usually have the following behavioral characteristics:
(1) These tokens are all created by the token factory contract using the createToken operation. In the createToken function, the following parameters need to be passed in when creating a token: token name, token symbol, precision, supply, token owner address, factory contract address for creating token pairs, and BUSD-T stablecoin address. The factory contract for creating token pairs uses PancakeSwap’s factory contract, and each token has a different owner address.
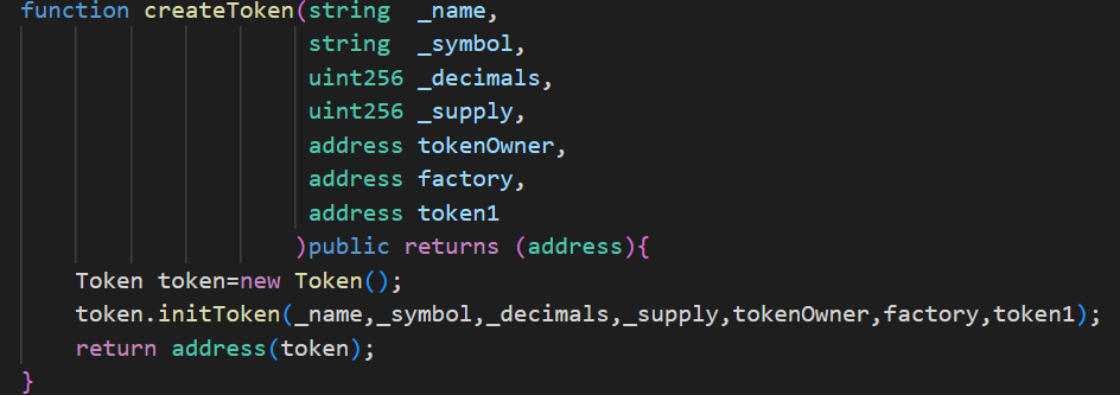
(2) Token owners use other addresses to perform batch buying and selling operations on Rugpull tokens. Under the buying and selling operations, the liquidity of the tokens will increase significantly and the price will gradually rise.
(3) Through phishing and other means of publicity, a large number of users are lured to buy. As liquidity increases, the token price doubles.
(4) When the price of the token reaches a certain value, the token owner enters the market to sell and perform Rugpull.
Behind this series of actions is a Web3 fraud gang with a clear division of labor, which constitutes a black industry chain, mainly involving hot spot collection, automatic coin issuance, automatic trading, false propaganda, phishing attacks, Rugpull harvesting and other links. The fake Rugpull tokens issued are closely related to industry hot events, and are highly confusing and inciting. Users need to be vigilant at all times, stay rational and avoid losses.
IV . Conclusion
The total loss caused by security incidents in the first quarter of 2024 reached 462 million US dollars. The increase in the price of coins this quarter and other factors have a certain impact on the increase in the total amount, but overall, the security situation of Web3 is not optimistic. Smart contract logic loopholes, Rugpull black industry chain, phishing attacks, etc. are the main reasons that threaten the security of users' encrypted assets. It is hoped that Web3 users and project parties can improve their security awareness as soon as possible to reduce losses.
Disclaimer: As a blockchain information platform, the articles published on this site only represent the personal opinions of the author and the guest, and have nothing to do with the position of Web3Caff. The information in the article is for reference only and does not constitute any investment advice or offer. Please comply with the relevant laws and regulations of your country or region.








