Original author: @BlazingKevin_, the Researcher at Movemaker
In 2026, the crypto industry stands at a new crossroads. With deep institutional investment, a settled regulatory framework, and the growth of AI in the on-chain economy, the privacy sector is undergoing an unprecedented paradigm shift. Over the past decade, blockchain privacy technology has often been misunderstood as a money laundering tool or a safe haven for hackers. This early form, based on "indiscriminate anonymity," has repeatedly suffered setbacks due to its inherent antagonism with the global financial regulatory system. However, the Privacy 2.0 paradigm, centered on "programmable compliance," has emerged and is becoming the cornerstone of the next generation of Web3 infrastructure.
1. The "Lost Decade" and the Logic Behind the Potential Explosion in the Privacy Sector
1.1 The Misconception of Indiscriminate Anonymity
Looking back over the past decade (2014-2024), the development of the blockchain privacy sector has been filled with idealism, but this has also led to its stagnation in commercialization. Early privacy projects, such as Monero and early Zcash, were heavily influenced by the Cypherpunk spirit, with their core design philosophy being "adversarial privacy." This thinking holds that privacy should be absolute and undifferentiated, and any form of regulatory backdoor or auditing interface is a betrayal of the spirit of privacy.
However, this technological approach has proven to be a false proposition in practice. Its core contradiction lies in its attempt to construct a completely black-box value transfer network within a system that needs to interact with the real-world financial system.
- A deviation in technological approach: Most Privacy 1.0 projects equate privacy with "hiding the transaction graph." For example, coin mixers sever the connection between senders and receivers by disrupting the flow of funds. This "privacy for privacy's sake" approach, while mathematically achieving anonymity, creates significant obstacles at the compliance level.
- The Achilles' heel of commercial expansion: Due to a lack of compliance boundaries, early privacy coins struggled to be accepted by mainstream exchanges and payment gateways. Driven by anti-money laundering compliance pressures, leading exchanges like Coinbase and Binance delisted privacy coins in multiple jurisdictions. This meant that privacy assets lost their liquidity entry point, becoming niche speculative tools or black market mediums, unable to support large-scale commercial activities.
1.2 The Lost Decade: The Mismatch Between Technology and Markets
The past decade has been called the "lost decade" for the privacy race because the industry invested too many resources in the wrong direction. Due to the overemphasis on "permissionless anonymity," most technological innovations (such as early ring signatures and simple zk-SNARKs transfers) focused on how to hide data more deeply, rather than how to manage data more flexibly.
This mismatch led to two results:
- Limited application scenarios: Aside from fund transfers and speculation, privacy coins have hardly built a rich ecosystem similar to DeFi, NFTs, or DAOs. This is because building complex financial applications on privacy chains that do not support programmability is extremely difficult.
- Regulatory arbitrage failed: Attempts to circumvent regulation through decentralized architectures have utterly failed. Regulators easily curbed the expansion of these protocols by cracking down on deposit and withdrawal channels and infrastructure service providers.
1.3 Defining "Programmable Compliance"
Entering 2025, the privacy sector experienced a structural recovery. This wasn't due to increased market demand for anonymity, but rather a qualitative shift in the essence of privacy technology. A new generation of privacy projects is building what's known as Privacy 2.0 , whose core feature is "programmable compliance."
"Programmable compliance" refers to embedding compliance logic (such as identity verification, blacklist screening, transaction limits, and audit report generation) directly into the underlying code or smart contracts of privacy protocols. It allows users to demonstrate the legality of their actions to specific regulators or counterparties while keeping their data confidential from the public.
This paradigm shift is reflected on three levels:
- Optional privacy: The system may be transparent by default, or allow users to selectively enable privacy protection, rather than a "one-size-fits-all" mandatory anonymity.
- Auditability: Users possess a "View Key" that they can proactively share with tax authorities, enabling them to decrypt and verify the transaction history of a specific account without disclosing it to the entire network.
- Rule embedding: Compliance rules can be enforced at the protocol level. For example, a privacy stablecoin contract can stipulate that "only addresses holding compliant DIDs (decentralized identities) can receive transfers," or "single transfers exceeding $10,000 require the generation of additional compliance proof."
1.4 The Inelastic Need for RWA Asset Tokenization
The tokenization of Real-World Assets (RWAs) is one of the biggest growth drivers for the Crypto industry in 2026. However, the large-scale on-chaining of RWAs faces an irreconcilable paradox .
- The pain point for institutions: Financial giants like BlackRock and Goldman Sachs would never trade on a completely public ledger like Ethereum. This would not only leak trade secrets but also lead to market manipulation and targeted short/long squeezes.
- The regulatory dilemma: Regulatory agencies (such as the SEC and ESMA) require financial transactions to be traceable and monitorable (meeting AML requirements), but at the same time, data protection regulations (such as the EU's GDPR) strictly prohibit the public release of customers' sensitive personal data on an immutable blockchain.
Privacy 2.0 is the only solution. Only through "programmable compliance" privacy technology can we achieve "confidentiality to the public and transparency to regulators."
1.5 Underlying Architecture in the AI Agent Era: Protecting Algorithms and Strategies
2026 is considered the starting year of the "AI Agent Economy." Thousands of autonomous AI agents will conduct transactions, arbitrage, and resource allocation on the blockchain. For these AI agents, privacy is no longer an option, but the foundation of their survival.
- Policy Protection: The core competitiveness of an AI Agent lies in its algorithm and trading strategy. If executed on a public ledger, its intent and patterns can be instantly identified by MEV bots and targeted (sandwich attack). Only in a privacy environment (such as Anoma's encrypted intent pool) can the Agent securely publish trading intents without exposing its strategy.
- Model privacy: Future AI agents may carry proprietary model weights or inference logic. Through zkVM (such as services provided by Boundless), agents can generate "proof of inference" demonstrating that their output is computed based on a specific model, without revealing the model itself. This is known as zkML and is key to the assetization of AI models.
1.6 Shift in Regulatory Attitude: From Banning to Regulating
Regulatory attitudes also underwent a subtle but significant shift in 2025-2026. Led by the EU's AMLR and MiCA, major jurisdictions worldwide began to differentiate between "Anonymity-Enhancing Tools" and "Privacy-Enhancing Technologies" (PETs) .
- The former is considered a tool for money laundering and has been continuously suppressed.
- The latter is considered compliance infrastructure and is encouraged. Discussions by agencies such as the U.S. Treasury Department also indicate that regulators are beginning to realize that the risk of data breaches from fully public ledgers is itself a systemic risk. Therefore, the technological approach supporting "selective disclosure" is gradually gaining acceptance.
2. Representatives from the three sub-directions of the privacy sector
Therefore, the explosion of the privacy sector is no longer just a hype, but an inevitable result of industry evolution. Following this line of thought, let's look at the strategic positioning of the following three projects:
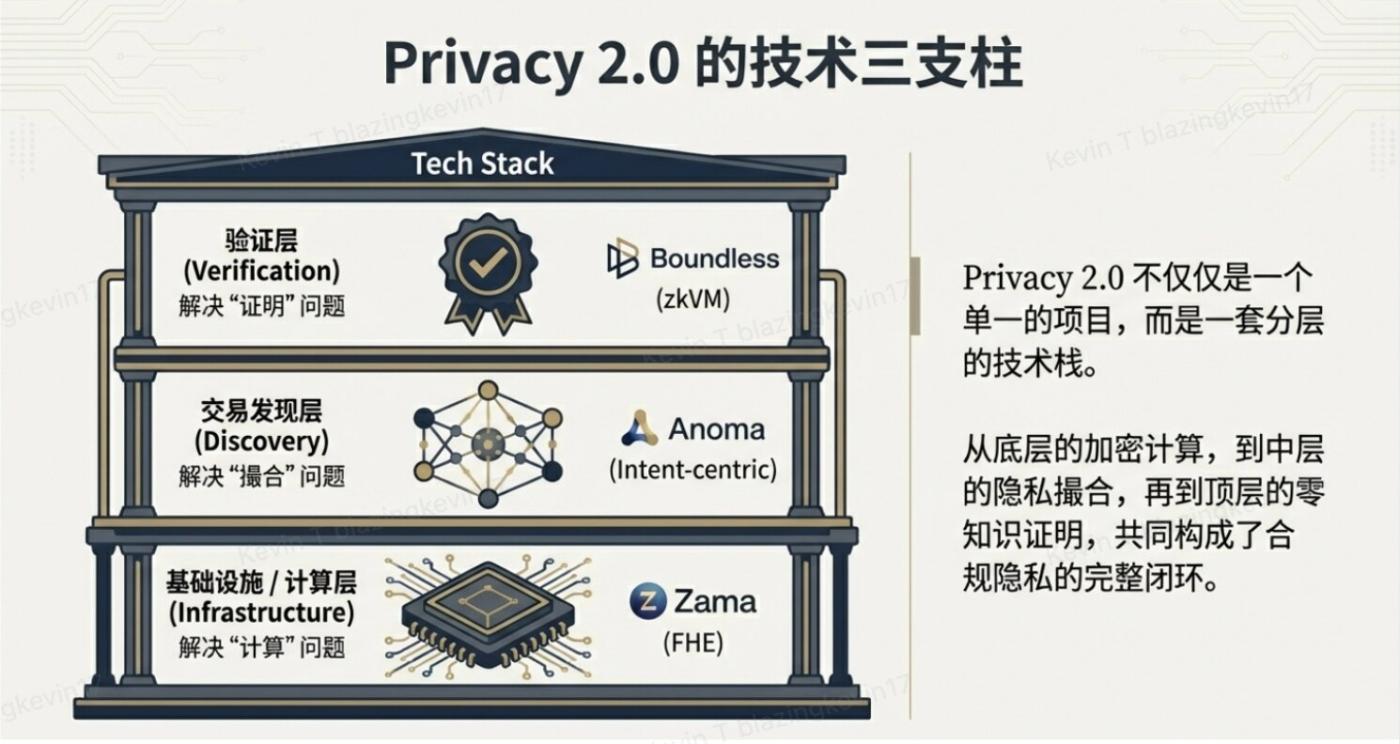
2.1 Infrastructure/Computing Layer: Zama
Source: Zama
In the Privacy 2.0 architecture, Zama occupies the core position at the very bottom—the computation layer. ZK solves the "verification" problem, while fully homomorphic encryption (FHE) solves the "computation" problem.
FHE enables applications to run business logic (such as lending, exchange matching, and voting) in a fully encrypted state, with node validators having no idea what transactions they are processing, thus completely solving the MEV and data leakage problems.
Zama's strategy is to create a "privacy plugin" for the entire industry, rather than launching a new chain. It aims to empower major public chains like Ethereum and Solana with the ability to process encrypted data.
Their biggest bet is currently on hardware, collaborating with Fabric Cryptography to develop accelerator chips to address the issues of slow speed and high cost. If this hardware solution can be implemented, FHE's operating efficiency will experience a qualitative leap, allowing the technology to be truly used by the general public, rather than remaining just a laboratory concept.
The current Zama is no longer just a theoretical concept. The recently concluded auction was essentially a "live-fire exercise" of FHE—using a cryptographic sealed-bid mechanism to match all bids "blindly" on the blockchain, directly and decisively eliminating the front-running and MEV chaos found in traditional auctions. With the TGE launch date set and mainnet staking enabled, Zama has officially completed its leap from "academic primitive" to "financial infrastructure."
With the previous acquisition of KKRT Labs, Zama is trying to integrate ZK and FHE. Once this closed loop of "privacy + computation + verification" is established, it will no longer be just a crypto project.
2.2 Transaction Matching Layer: Anoma
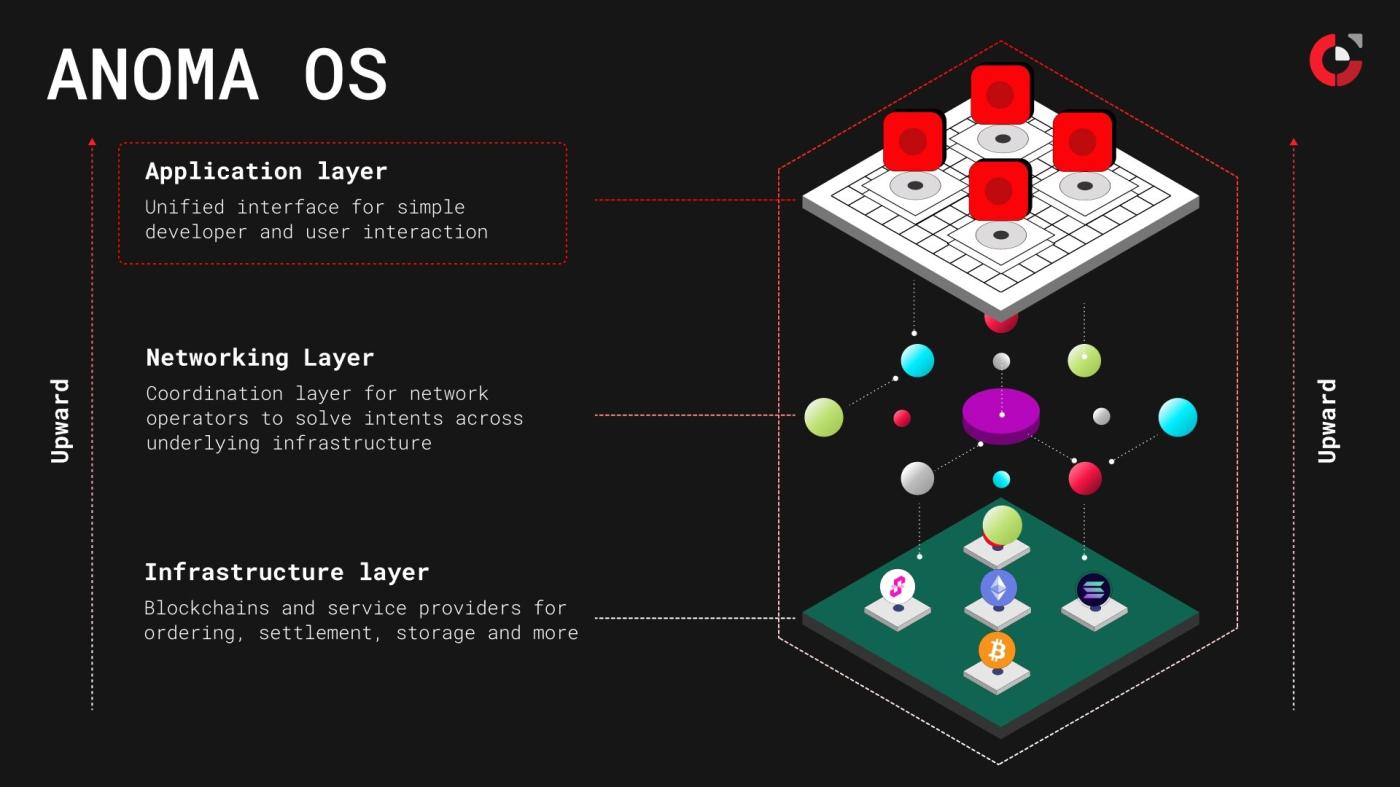
Source: Anoma
If Zama solved the problem of data confidentiality , then Anoma focuses on solving the discovery and matching mechanisms for transactions.
Traditional DeFi users' transactions are typically exposed directly within Mempool, with their intentions fully revealed to the MEV bot. Anoma, on the other hand, allows counterparties to discover privacy; users publish encrypted intentions, and the Solver matches transactions without decryption (combining FHE or TEE).
It's clear that this solution only addresses the basics of privacy; it also solves the problems of multi-chain fragmentation and interaction complexity.
Once a user's transaction intent is publicly disclosed in the Mempool, they become prey for MEV bots. Anoma introduces an "intent center" architecture. Users no longer sign transactions, but instead sign "intents." Intents can be encrypted. They are only decrypted and executed when specific conditions are met. This means that MEV bots cannot peek into a user's hand and therefore cannot launch preemptive attacks.
Anoma recently completed its integration with the Base mainnet, extending its intent settlement layer to the EVM ecosystem and thus reaching a wider liquidity market. The current technical focus is on the final activation of the "protocol adapter." As a core component connecting user intent and Solver execution, the adapter's launch will mark the completion of the network's functional loop—at which point $XAN will transform from a simple governance credential into a utility token used to pay network settlement fees. Its ability to effectively handle the matching needs of multi-chain transactions remains to be seen.
2.3 Verification Layer: Boundless
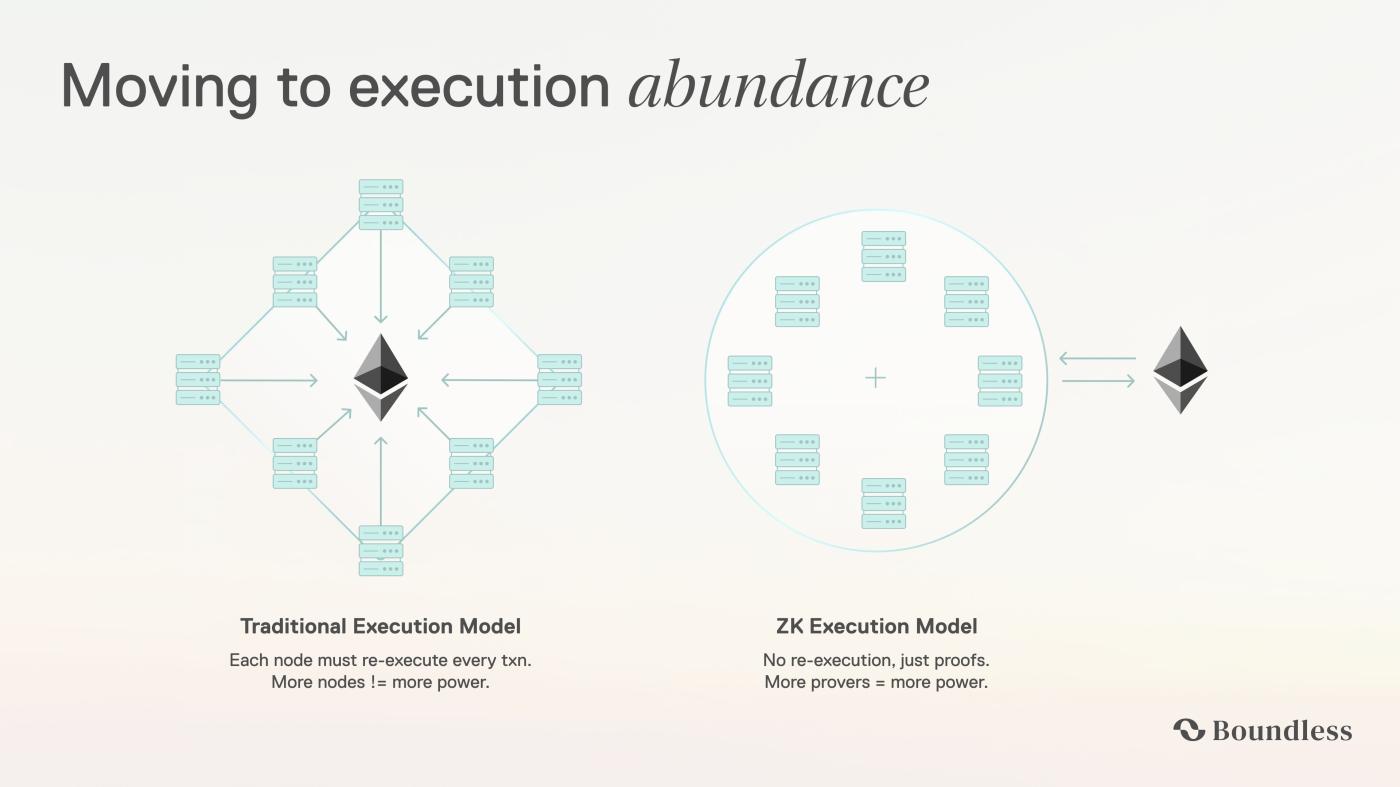
Source: Boundless
With the proliferation of ZK Rollups and various privacy applications, the computationally intensive "Proving" process has become the biggest obstacle. Boundless was created to address this challenge, specializing in the large-scale production of "universal privacy proofs".
Boundless transforms the ability to generate ZK proofs into a tradable computing power commodity , modularly embedding it into all scenarios that are hungry for ZK verification.
- Operating Mechanism: This is a free market for computing power. Developers post their computing needs (such as verifying a privacy ledger or running an AI model), and Provers in the network enter the market with GPU/FPGA computing power to bid for the task, generate proofs, and ultimately put them on the blockchain.
- Unified Interface: It's like Chainlink in the ZK computing world, providing a standardized proof service layer for all blockchains. Any chain can "outsource" its heavy ZK workload simply by making API calls.
As demand for ZK-Rollups and ZK Coprocessors explodes, Boundless will become the decentralized engine handling massive volumes of ZK proofs. It completely unlocks the limits of imagination for privacy applications: whether it's on-chain identity, credit assessment, compliance review, or AI Agent policy verification, zkVM can provide them with a protective shield of privacy.
Boundless leverages BitVM to upgrade Bitcoin to the ultimate settlement layer for ZK proofs. This is not merely a technological upgrade, but a strategic leap: it is no longer limited to being a coprocessor within the Ethereum ecosystem. Once this decentralized Prover Market is operational, Boundless will anchor high-load AI inference and complex financial model computations to the absolute security of Bitcoin.
3. If the privacy sector is officially recognized, its competitive advantage may be amplified.
Having understood the strategies employed by Zama, Anoma, and Boundless, we need to examine the ultimate outcome of the privacy race from a higher perspective. Privacy will create the most powerful "chain-locked" effect.
3.1 Differences in network effects between public blockchains and privacy blockchains
On public blockchains, the migration costs for users and assets are extremely low. Because all data is publicly transparent, cross-chain bridges can easily verify state and transfer assets. This has led to competition among public blockchains other than Ethereum, Solana, and BNB becoming a simple competition of performance and fees, resulting in shallow competitive moats. Users are essentially "mercenaries," going wherever the returns are highest.
But on the privacy chain , the situation is quite different.
3.2 "Chain Locking" Mechanism: Why Privacy is Difficult to Across Chains
"Cross-chain tokens are easy, but cross-chain privacy is difficult."
When a user accumulates a large amount of encrypted state (such as encrypted credit records, private transaction history, and undisclosed holding strategies) in a privacy ecosystem (such as a chain based on Zama fhEVM), it is difficult for him to migrate these "secrets" to another chain.
- Metadata leakage risk: Even if cross-chain technology is technically possible, the migration process itself generates metadata. Monitors can infer a user's true identity by analyzing characteristics such as the timing, amount, and frequency of fund inflows and outflows. This is known as the "deanonymization risk of fund inflows and outflows."
- State non-portability: Encrypted data often relies on a specific chain's key management system (such as Zama's threshold decryption network). To migrate data, it must first be decrypted (exposing the risk) and then encrypted on another chain. This high risk cost constitutes an extremely high barrier to conversion.
This characteristic of "being able to get in but not being able to get out" (or "not daring to get out") creates strong user stickiness.
- Stronger network effects: In privacy networks, the more users there are, the larger the anonymity set becomes, and the stronger the privacy protection for each user. This is a positive cycle: better privacy -> more users -> better privacy.
- Winner-takes-all: Due to extremely high migration costs and strong network effects, the privacy sector is unlikely to see a "hundred flowers bloom" scenario, but is more likely to evolve into a "winner-takes-all" situation. A few leading privacy infrastructure companies will capture the vast majority of the value.
The privacy race in 2026 is an essential step for Web3 towards a mature financial system. Reborn from the ruins of Tornado Cash is a new generation of Privacy 2.0 , equipped with FHE (computation), Intents , and zkVM (proof) . The core driver of this transformation is "programmable compliance," which aligns with the demands of the era of RWA asset on-chaining and the explosion of AI agents.
About Movemaker
Movemaker is the first official community organization authorized by the Aptos Foundation and jointly launched by Ankaa and BlockBooster, focusing on promoting the construction and development of the Aptos ecosystem in the Chinese-speaking region. As the official representative of Aptos in the Chinese-speaking region, Movemaker is committed to building a diverse, open, and prosperous Aptos ecosystem by connecting developers, users, capital, and numerous ecosystem partners.
Disclaimer:
This article/blog is for informational purposes only and represents the author's personal views, not the position of Movemaker. This article is not intended to provide: (i) investment advice or recommendations; (ii) an offer or solicitation to buy, sell, or hold digital assets; or (iii) financial, accounting, legal, or tax advice. Holding digital assets, including stablecoins and NFTs, carries extremely high risk, with significant price volatility and the possibility of becoming worthless. You should carefully consider whether trading or holding digital assets is suitable for you based on your own financial situation. For specific questions, please consult your legal, tax, or investment advisor. The information provided in this article (including market data and statistics, if any) is for general informational purposes only. Reasonable care has been taken in preparing these data and charts, but we are not responsible for any factual errors or omissions expressed herein.







