似乎: 1. 0x9cb8d9BaE84830b7f5F11ee5048c04a80b8514BA 属于/与 @0xswapnet 相关:swapnet-1.gitbook.io/docs/refe...… 2. 0xbeef63AE5a2102506e8a352a5bB32aA8B30B3112 属于/与 @ApertureFinance 相关:github.com/Aperture-Finance/un...…
本文为机器翻译
展示原文

BlockSec Phalcon
@Phalcon_xyz
01-26
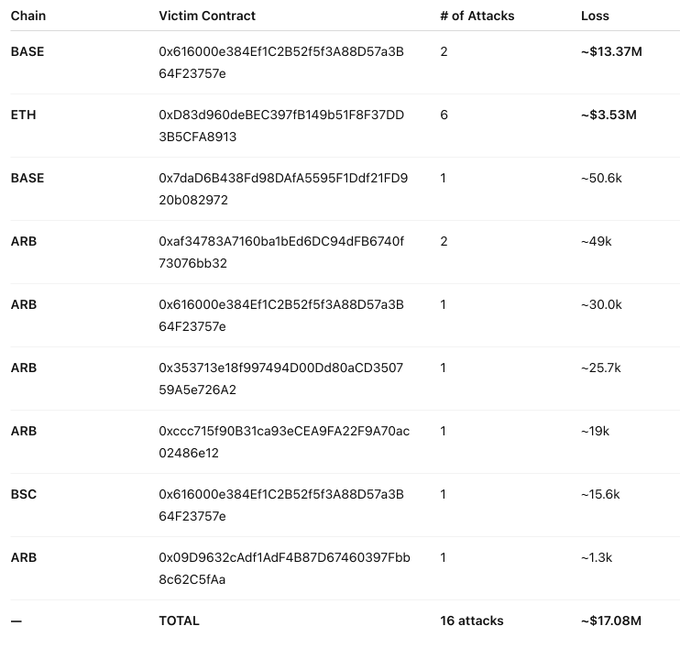
ALERT! We detected a series of suspicious transactions hours ago targeting victim contracts deployed by two creators across #Ethereum, #Arbitrum, #Base, and #BSC, with total losses exceeding $17M.
The victim contracts are not open-source and appear to expose an arbitrary-call
来自推特
免责声明:以上内容仅为作者观点,不代表Followin的任何立场,不构成与Followin相关的任何投资建议。
喜欢
收藏
评论
分享