Recently, we have been hearing a lot about MEV bots and how they managed to make millions in price arbitrage. In this week’s digest, we will cover the basics of MEV bots, what they are, who uses them, and how they make money.
What are MEV bots?
Traders from both TradFi and DeFi are very familiar with automated arbitrage trading, an algorithm spotting price discrepancy between exchanges to then buy low and sell high, making a profit from the differences. Particularly, in the DeFi market where price volatility is high and trading occurs 24/7, these bots are deployed at a larger scale with more avenues to generate profits.
These are called MEV or Maximal Extractable Value bots, designed to maximize profits within the public blockchain they are operating in.
There are 2 main demographics who deploy and profit from MEV bots in public blockchains.
Validators: Essentially, validators are responsible for verifying transactions and creating new blocks in the blockchain. Hence they have the ability to prioritize transactions that generate higher fees or MEV rewards or create opportunities for themselves or their affiliated bots to capture value. Additionally, they may delay validation of certain transactions, creating additional MEV opportunities for bots.
Searchers: An individual on the network who uses complex algorithms to find profitable MEV opportunities and has bots that automatically send these transactions to the network. They are not validators, but they pay high gas fees to validators to increase the chances of their transactions being included in a block.
Together, they deployed MEV bots to execute various profit-maximizing techniques such as:
Front-running: MEV bots will detect profitable pending transactions and execute similar transactions ahead of others, enabling them to benefit from price movements or other opportunities before others in the queue.
Sandwich Attack: MEV bot places orders before and after a pending transaction to profit from the resulting price movements. For instance, if a large buy order causes the price to increase, the bot can buy low and sell high by placing a buy order before the trader's transaction and a sell order after it.
Liquidation: MEV bots exploit liquidation opportunities by monitoring situations where assets are sold to repay loans. For example, if a trader's assets fall below a certain threshold and their loan is liquidated, the bot can buy these assets at a discount.
Profit from these bots can be lucrative. In April 2023 alone, MEV bots generated approximately $7.4 million in profits on the Ethereum blockchain, with sandwich attacks being the most prominent technique according to EigenPhi.
Why should exchanges be concern?
Short-term gains for these bots often translate to long-term business risk for exchanges as the methods they deploy to generate profit often come at the cost of retail investors who could not compete with the bot's efficiency and capabilities, discouraging them from further participation.
Once retail investors are driven away, trading volumes will go down, and the bots will move on to other opportunities, leaving the exchange with little to no users, raising the incentive for exchanges to set up guard rails against MEV bots.
For retail investors, being knowledgeable about MEV bots could better serve to inform risk-adjusted trading strategies and the selection of which exchange to trade on.
Last Week’s Incidents
🚨Project: BeatGen
⛓️Chain: BSC
💥Type: Business Logic Flaw
💸Loss amount: $14,000
Last week, a blockchain-based music platform called BeatGen was hacked for $14,000. The incident was caused by a function called "convertUsdBalanceDecimalToTokenDecimal()" in the oracle.sol file. It mistakenly increased the "amountTokenDecimal" variable due to a reduction in the "balanceStableToken" denominator caused by a flash loan. The project has yet to address the hack on its social media.
🚨Project: OceanLife
⛓️Chain: BSC
💥Type: Reflection Token
💸Loss amount: $10,500
A project called OceanLife was hacked for $10,500. The hacker was able to increase the balance of the pool by calling the _reflectFee function when transferring $OLIFE, which reduced the total amount of _tTotal. As a result, the hacker could withdraw a significant amount of $WBNB from the pool by calling the swap function directly after accumulating the increased balance. The project’s social media last update was in 2021 and its website is no longer available.
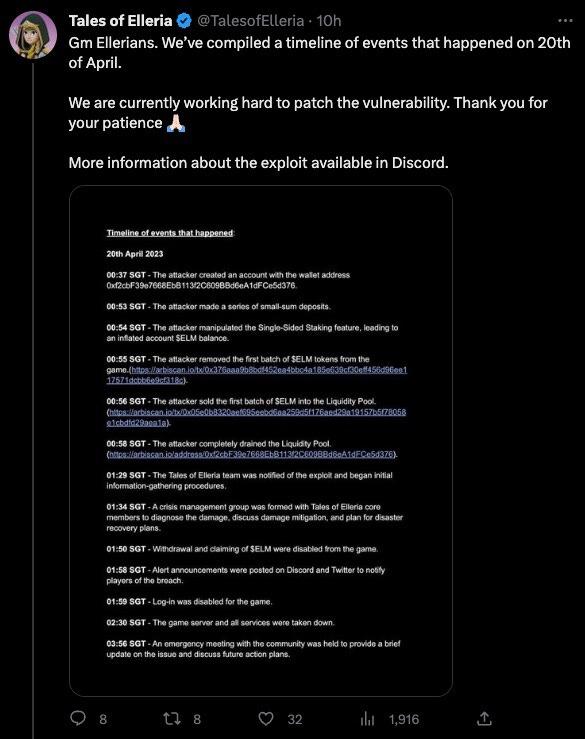
🚨Project: Tales of Elleria
⛓️Chain: Arbitrum
💥Type: Stake Exploit
💸Loss amount: $270,000
The largest hack last week occurred on a Web3 game called Tales of Elleria, losing $270,000. The attacker used the wallet address Oxf2cbF39e7668EbB113f2C609BBd6eA1dFCe5d376 to perform several small-sum deposits. By manipulating the Single-Sided Staking feature, the attacker was able to inflate their account's SELM balance. Next, the attacker removed the initial batch of $ELM tokens from the game and sold them into the Liquidity Pool. Finally, the attacker drained the entire Liquidity Pool, resulting in a complete depletion of its funds. The game developers are currently patching the vulnerability and are looking into compensation methods.