On May 16th, Ledger unveiled its latest feature, Ledger Recover, sparking controversy and misunderstandings around the concept of "trustlessness" in hardware wallets and security concerns associated with the recovery feature. Verichains aims to provide market clarity on trustlessness in hardware wallets and the security implications of introducing a feature that grants direct access to your private keys.
What Are Hardware Wallets?
A hardware wallet is a physical device that lets you store private keys and execute crypto transactions. Contrary to its software counterpart, a hardware wallet is categorized as “cold storage” as it is not connected to the internet thwarting any attempt of hacking or exploitation and limiting them to only physical threats. Consumers generally consider hardware wallets as trustless solutions, as they solely rely on themselves to manage wallet security and by extension, their private keys.
A hardware wallet consists of two components: the hardware itself and the software. The hardware includes buttons, a screen, an enclosure, and most crucial of all, the Secure Element that protects the device against physical attacks.
The secure element is typically a tamper-resistant chip with its dedicated processor, memory, and cryptographic functionalities, or in other words, a tiny computer that is really secure. It is designed to resist physical and logical attacks, providing protection against unauthorized access, tampering, and extraction of sensitive data.
On the software side, the hardware wallet requires an operating system (OS) to function. The OS establishes a secure digital environment for storing private keys, managing the device logic, and facilitating communication between the hardware wallet and its software extensions on computers or smartphones.
Ledger Recover
To summarize the situation, in a move to make the crypto experience more digestible to newcomers, Ledger introduced Ledger Recover, an optional feature allowing users to recover their private keys similar to password recovery. However, this announcement received backlash from the crypto community and Ledger customers, who argued that the service would compromise the self-custodial nature and introduce additional risks. To comprehend the security implications of Ledger Recover, it is crucial to understand its functionality. The process involves encrypting and splitting the Secret Recovery Phrase into three fragments, which are then transmitted through separate secure channels to backup providers. Each fragment is stored by a different company in different countries, ensuring no single entity possesses the complete backup. These encrypted fragments are kept in tamper-resistant servers known as Hardware Security Modules.
To verify a user's identity, Ledger Recover utilizes an Identity Verification provider called Onfido. User identification, including an ID and selfie, undergoes encryption and is stored securely. This enables the service to link the user's identity to the encrypted fragments of the Secret Recovery Phrase, ensuring only the user can recover their private keys. When users want to restore their wallets, they initiate the recovery process from Ledger Live.
What Are The Risks?
In a tweet responding to the announcement of Ledger Recover, Verichains Co-founder Thanh Nguyen commented that this feature raised serious concerns regarding the security of a user’s seed phrase and breaks the common security assumption in relation to hardware wallets.
Let’s further elaborate on this idea and discuss the risk associated with Ledger Recover.
Private Key Exposure: Hardware wallet users commonly assume they are the only ones capable of accessing their private keys and safeguarding their wallet's secret recovery phrase. However, the introduction of a recovery feature challenges this assumption by sharing the recovery phrase with two different parties, regardless of prior fragmentation.
Introduction of New Risks: With more features, the potential attack vectors increase. In the case of Ledger Recover, which grants direct access to users’ wallets, the stakes are high. The encrypted fragments of the Secret Recovery Phrase are stored by two separate companies in different countries, introducing two potential attack vectors. A determined attacker might attempt to exploit vulnerabilities in these companies and gather multiple fragments to gain access to the Secret Recovery Phrase.
Universal Target: Although Ledger Recover is an opt-in feature, it exists among all Ledger customers, creating unease for those who do not wish to participate. The possibility of vulnerabilities in this feature cannot be entirely dismissed.
With much backlash from the crypto community, Ledger postponed the launch of its new feature and will relaunch when its source code is open and auditable. However, even if the open-source code passes security audits, there is no guarantee that it is free from vulnerabilities.
From our experience as security researchers, there is always a possibility of hidden vulnerabilities residing within open-source libraries. Most notably, our recent discoveries of critical key extraction attacks in Popular Threshold Signature Scheme for MPC Wallets and Digital Asset Custody which can be found in popular open-source libraries.
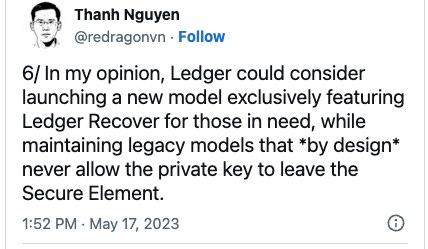
In the same Twitter thread, Thanh also suggests that Ledger should consider launching a new model that caters exclusively to users who wanted to opt into Ledger Recovery, while maintaining legacy models that are by design, never allowing the exposure of the Secret Recovery Phrase. This ensures users who opted out of this feature will be insulated from any potential risk that is associated with Ledger Recovery, especially when a vulnerability is found or exploited.
Entirely Trustless?
Recent controversies point toward Ledger’s hardware wallets are not entirely trustless, subverting the security assumption of many in the community. This is true from the beginning as some level of trust is still necessary in the wallet/software provider. Like any software, a firmware update from the product provider is always warranted to ensure the security, compatibility, and functionality of the device. In the case of Ledger or any hardware wallet provider, a firmware update will modify the OS or application within the Secure Element, potentially granting access to the seed phrase. Thus, a certain level of trust in Ledger is required for them to provide good-faith firmware updates.
In addition to the new recovery feature from Ledger, ultimately, the decision to trust Ledger and its partners with safeguarding users’ Secret Recovery Phrase and, by extension, their private keys is an exercise of trust and risk tolerance. How much trust are users willing to give Ledger and its partner in safeguarding their Secret Recover Phrase, and how much risk are users willing to tolerate for an improvement in ease of use and accessibility? Users must evaluate their security and utility needs to make an informed decision about opting for Ledger Recover or considering an alternative hardware wallet.